All of us use passwords daily. Have you ever paused and thought, “How secure is my password?” Passwords are the keys to our digital lives and help us access everything from email accounts to online banking websites.
If a hacker gains access to your password, they could steal your identity and other personal data. Even if nobody has stolen your password before, it's a good idea to consider what makes a strong password in the first place.
Why Strong Passwords Are Important

Strong passwords, like strong locks, are the first line of defense against cybercriminals. Just like buying a secure lock for your home, you should keep strong passwords in your digital life. If your password is weak, hackers can easily guess it and gain access to your accounts.
Imagine if someone cracks or steals the password to your email account. The thief can easily reset all your other passwords with access to that account. Or if they access your online bank account, they can steal all of your money in minutes.
Using a weak password is simply inviting trouble.
How Secure is My Password?
Because of the many password possibilities, we can't tell you how strong yours are. In any case, you shouldn't be telling us your passwords. Instead, use a reputable tool that can check your password strength.
Note: Be careful of what tools you use to check your passwords. Try to avoid any password checkers that don't originate from known cybersecurity companies.
Here are some reliable password security checkers that you can try;
- LastPass password security checker
- NordPass password security checker
- Kaspersky password security checker
Understanding Password Strength
A strong password is a password that is difficult to guess or crack. However, just because a password is long doesn't necessarily mean it's secure. Length isn't the only factor that makes a password strong or weak.
There are several parts to what makes a strong password;
Password Length
A longer password is more robust than a shorter one because there are more possible characters in a long string than in a short string. For example, let's say you have a 10-character password that uses only lowercase letters (26).
This configuration allows for 26*10 = 260 possible combinations. That might seem like a lot, but if someone tries to crack your password by randomly guessing it, they can test all 260 possibilities in less than one second.
Password Complexity
A complex password combines many different component elements. The more complex the password, the more secure it is. For example, the most secure passwords include upper and lowercase letters, numbers, and special symbols.
For example, “password” has six characters but no variation in character types (it's all lowercase). On the other hand, “p@55w0rd” has eight characters and four different types (lower case letter, upper case letter, number, and a special character).
Password Randomness
The more random a string of characters is, the less likely someone could guess it based on patterns in words or phrases you might find. Hackers, for example, might use dictionary words as the basis for their password-cracking activities.
Randomness makes it more difficult for hackers because they cannot predict what kind of character will come next. For example, a randomly generated password will look like this: J/@?a+N;fvx!QT9ZRJgB2hmr6zr+]#hJ*Aj.
How Hackers Crack Passwords
There are many ways hackers and other cybercriminals can crack or steal your passwords. Some methods are more direct than others, and all have varying degrees of success. Here are some common methods hackers use;
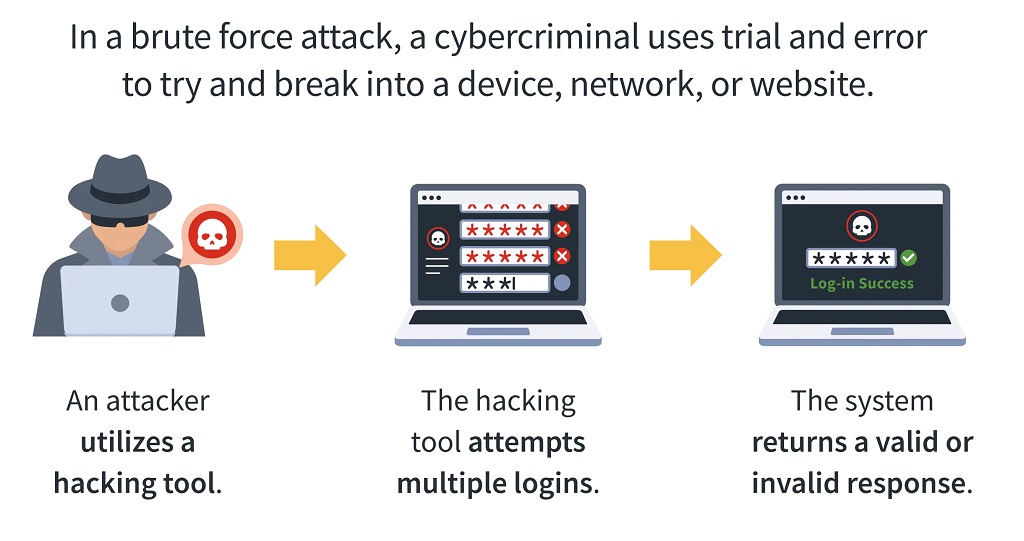
Brute Force Attacks
The brute force attack is a crude and straightforward method that was one of the first to emerge. Hackers simply use a program to try every possible password combination until they find one that works. This method is highly inefficient and can require a lot of time and computing power.
In reality, hackers don't use brute force attacks very often — they're too slow and easily detectable by modern computer systems. Instead, they rely on other methods to guess your password.
Dictionary Attacks
A dictionary attack is similar to a brute-force attack with a few modifications. Instead of trying random passwords, it uses lists of words or phrases commonly used as passwords (like “password1234”) to guess your password.
These methods are mainly obsolete today since hackers have a much more comprehensive range of tools. One good example is the Phishing Attack. Instead of trying to crack a password, hackers fool users into handing those passwords over.
In a phishing attack, an attacker sends you an email with a link that looks like it's from your bank or another service provider asking for your login credentials. However, this link takes you to a fake website where the attacker will record the details you provide.
Common Poor Password Practices
Password management is one of the most critical aspects of cybersecurity. Bad passwords are a big problem, but many other common password malpractices can also hurt your security.
Here are some things you should avoid when creating and managing passwords:
Reusing the Same Password
Using the same password for all your online accounts is a common practice. Complex passwords can be a headache to remember. As a result, many people create one strong password and use it for all their online activities.
The problem with this is anyone who hacks or steals that password immediately gets access to your entire digital portfolio. And if you discover that the password is compromised, you need to change your password for every single website and service.
Never Changing Your Passwords
If you never change your passwords, anyone that's determined enough will crack it sooner or later. Even the most robust password will eventually wear down. Because of this, it's advisable to go through renewal cycles to update your passwords periodically.
For those who worry about not being able to remember all those complex passwords, use a password manager like NordPass or LastPass.
Not Changing Default Passwords
Many services and devices we use today come with default passwords. Examples include your wireless router, WiFi adapters, and such. These default passwords are for your convenience and not typically strong enough to withstand a hacking attempt. Always change default passwords as soon as possible.
Using Sequential Numbers or Characters
Using a simple string of sequential numbers or characters is easy to remember. While it may seem like a good idea, sequential passwords are the easiest to crack. A hacker with the most rudimentary tools can easily brute force a sequential password.
Writing Down or Saving Password Records
While it may seem like a good idea if you forget them, keeping password records written down or stored on your computer is bad. Files and pieces of paper can be lost or stolen easily. If you can't remember your passwords, store them securely with a password manager.
Password vs. Passphrase – What's the Difference?
Users' biggest complaint about passwords is that they are too easy to guess. But here's a question: are you using passwords or passphrases on your computer? Aren't they essentially the same thing? Well, not exactly.
Passphrases are more secure and challenging to crack than passwords because they are longer and highly randomized. The difference is apparent even if you're using only characters. Compare these two examples;
Password: “dog”
Passphrase: “dog cat rabbit fish”
As you can see, the passphrase adds a lot of depth to your security. Once you add in extra elements like randomness and complexity, passphrases are nearly unbeatable.
Conclusion: Your Password is as Secure as You Design it to Be
So, how secure is your password? To keep your information and data safe, you should ensure it's robust. You'll also need to change it regularly. What we've covered here can help you decide what makes a good password, but ultimately there are no hard-and-fast rules—only best practices.
You can use whatever method works for your organization or personal needs; remember that any password should be difficult for hackers. As for you, that's something you can handle with a good password manager.
Also Read;