Everyone is a target in today's cyberwar climate. Over 255 million phishing attacks occurred in 2022 alone, a 61% increase compared to the previous year. These aren't going to stop, so the best way to stay safe is to learn how to recognize phishing emails.
Phishing has been a common attack vector for cybercriminals for years. Despite the advancements in technology, phishing attacks are increasing. Cybercriminals leverage helpful technological advancement to churn out even more sophisticated and complex attacks.
To help combat such phishing attacks, learn these eight ways of recognizing phishing emails;
1. Sender Uses a Public Email Domain
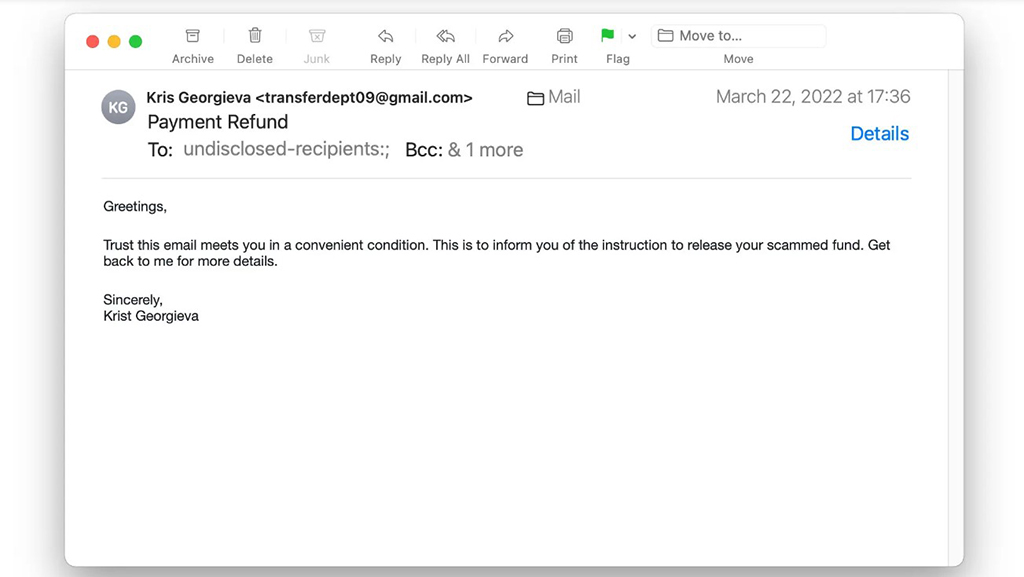
Legitimate companies have domain-specific emails. While verifying the sender's name, remember to check the email address. If the sender uses a public email domain, such as “@gmail.com” or “yahoo.com,” you have every right to doubt the email's authenticity. Legitimate organizations usually do not send emails from an address that ends with a public email domain.
The email above shows an example of a sender wanting the recipient to revert for a refund. Notice that the sender is using a public email domain. You should be suspicious. Even smaller companies tend to use third-party email providers with a custom domain. Businesses will seldom use public email services.
2. Sender Uses a Conflicting Email Domain
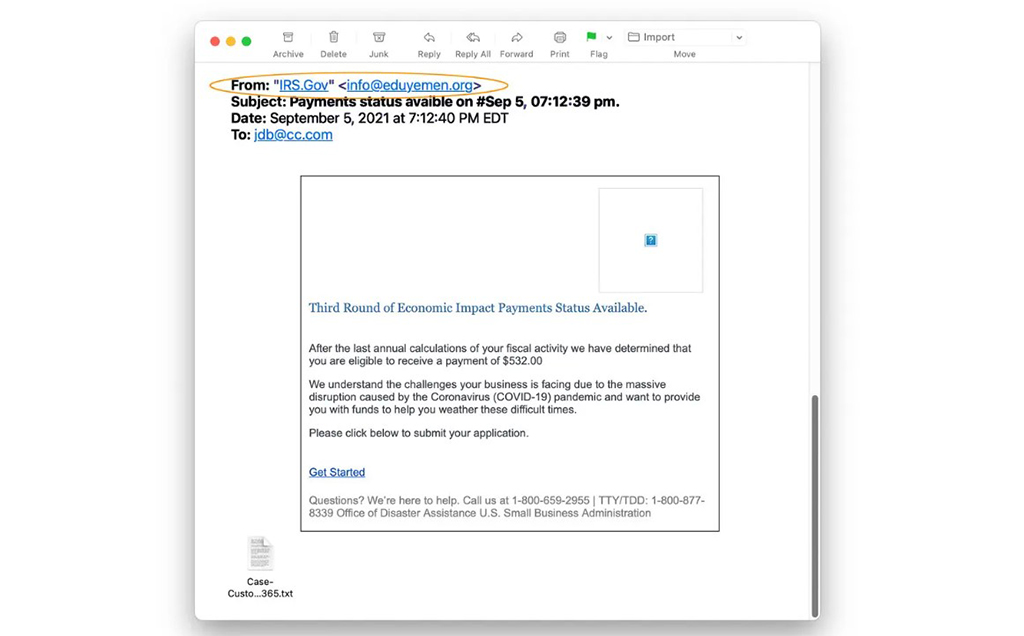
If the sender's email address is not associated with the domain name of the sender's company, you should be on the alert. Most legitimate emails use a domain that matches the name of the organization.
Even though the sender isn't using a public email domain, be alert if the sender uses a conflicting email domain. Take, for example, the email in the image above. The sender's name and the email address domain are incompatible.
If this is a legitimate email, the domain name should be IRS-related, but it isn't. Hence, do not click anywhere on the email and report it; this is a phishing email.
3. Misspelled Sender's Domain Name
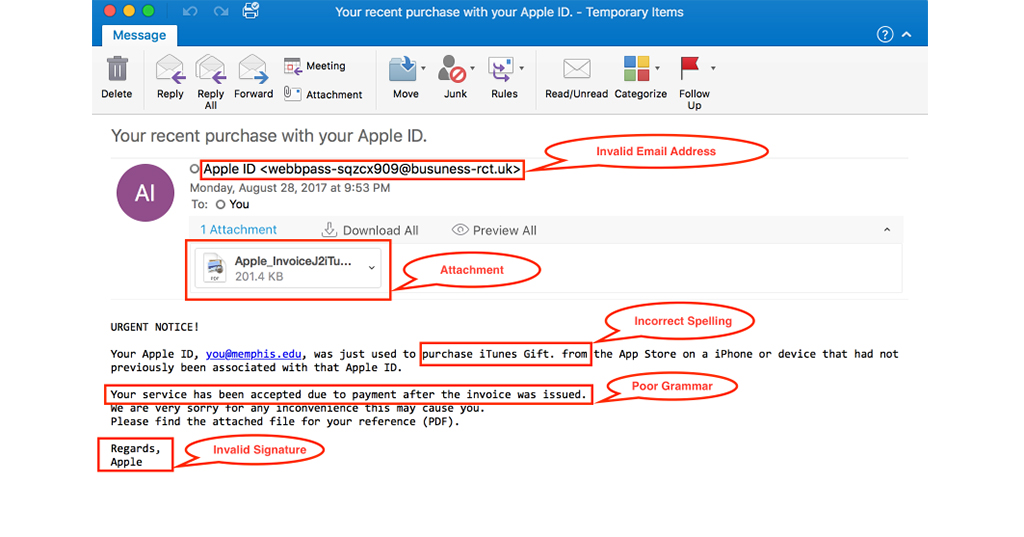
Dwelling on the email domain name here again is proof of how strong an indicator it can be to help you spot phishing scams. We often glance through an email quickly, which is understandable since we have so much to do. However, an instant of being meticulous can save you and your company.
Hackers use an email address that looks like the original, with a letter or two changed, added, or removed. If you're not careful, your eyes swiftly drift through the words, and your brain processes them as the correct domain name.
The next is history; you fall into the trap, hook, line, and sinker. As such, pay attention to these nitty-gritty details. You'll be thankful you did.
The example above is from a supposedly Apple employee alerting on a so-called dubious transaction. Before you even read further, take note of the email domain. Instead of “business,” it spells “busuness,” an obvious spelling error many often overlook.
4. Emails with an Urgent Tone
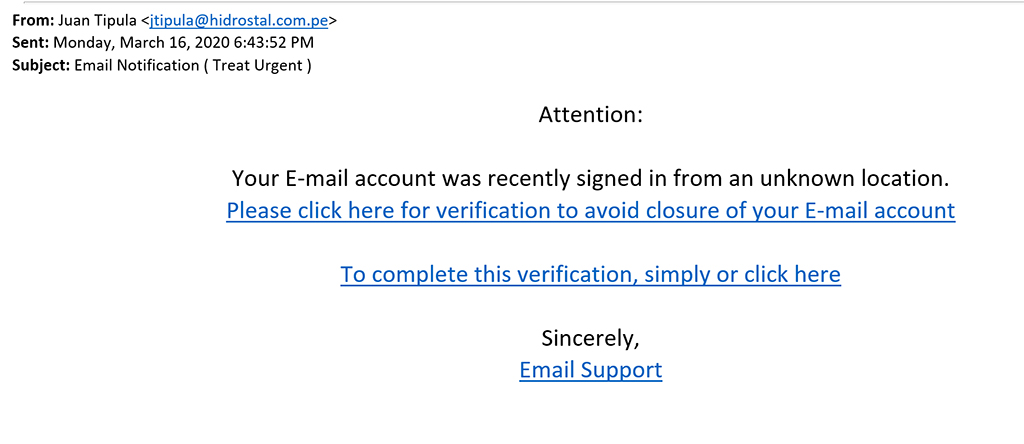
Emails demanding urgent action on your part or threatening a negative consequence unless you immediately take action are often signs of phishing emails. Hackers prey on the psychological aspect to push you into acting promptly. This manufactured sense of urgency creates anxiety, forcing you into action.
The hackers' goal is to overwhelm you and not want you to dwell on the email for potential flaws or inconsistencies. The imposed time limit and uncharacteristic sense of urgency give a false sense of urgency. Unfortunately, many fall for this.
The above shows an example of an email with an urgent tone reporting an issue of a suspicious login attempt. The urgency is amplified by threatening to close the email account if you do not promptly act. Phishing scams like this are dangerous as many are hasty to fall prey to such “urgencies.”
5. Dubious Attachments or Links
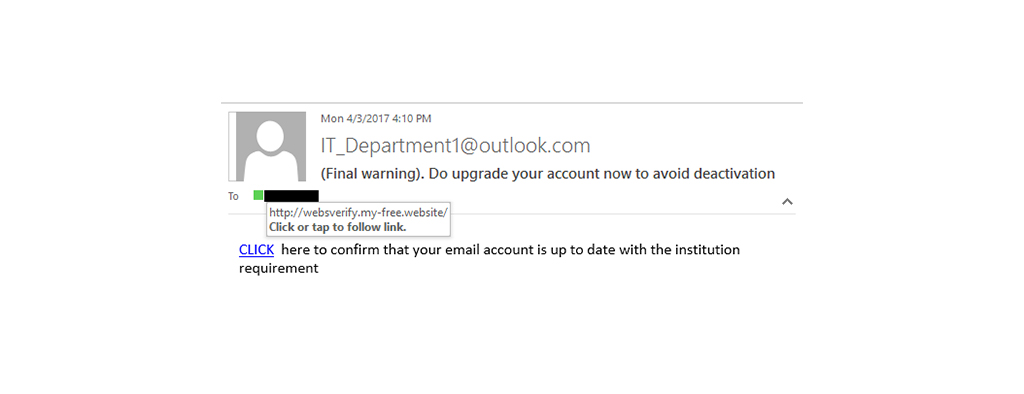
Beware when clicking any links or attachments in your emails – a sound advice. Phishing emails incorporate links that may seem harmless but direct you to a mockup website that prompts you to input your personal information; this is where they steal your data – identity/data theft. Most would hide the link behind seemingly genuine CTA buttons too.
Some ways can help you identify phishing emails in such circumstances. The first thing is to find out where the links/buttons go before clicking them. You hover your mouse over the button or link. Then take note of the destination address at the bottom of the browser. If the destination address does not match the context of the email, alarm bells ring.
The example above from Mount Saint Vincent University proves that the CLICK link points to a conflicting destination from the context of the email. Any URL with ‘free' in them suffices to raise red flags.
Also, most legitimate emails direct you to their official website to download files instead of including attachments. Hackers rely on your curiosity; you won't know its content until you open the attachment. However, attachments can be malware-infected.
Do not open any attachments unless you are confident of the email's authenticity.
That said, this method isn't foolproof, as there are instances where legitimate companies send you information via attachments or links. Whenever in doubt, always contact the sender directly for confirmation.
6. Badly Written Emails
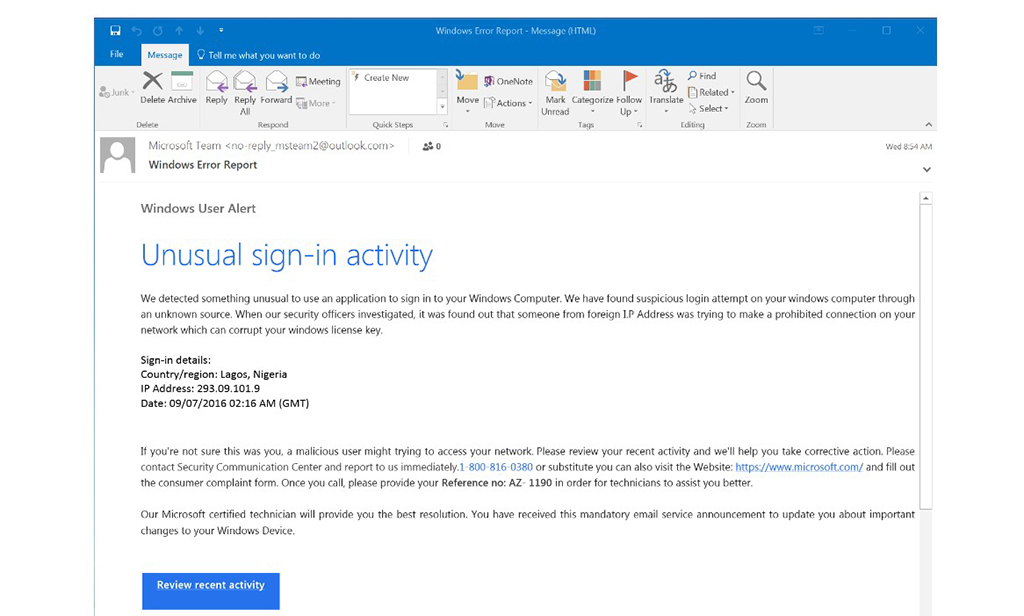
Phishing emails are usually poorly written due to hackers needing better writers. Hence, it is not surprising that such emails contain typo errors, spelling mistakes, and bad grammar. Of course, there are times when such errors are genuine.
Some hackers use a spellchecker or translator tool, which may give them all the right words but may be contextually incorrect. Always verify the email contents if something sounds “off.”
Could this be a typo error, like accidentally hitting an adjacent key? Any differences from the usual previous emails? Ask yourself questions to dig in deeper.
Look at the Windows email above entitled “Unusual sign-in activity.” There are notable missing words and grammatical errors. An official message written like this is almost certainly a scam.
7. Emails Requesting Sensitive Information
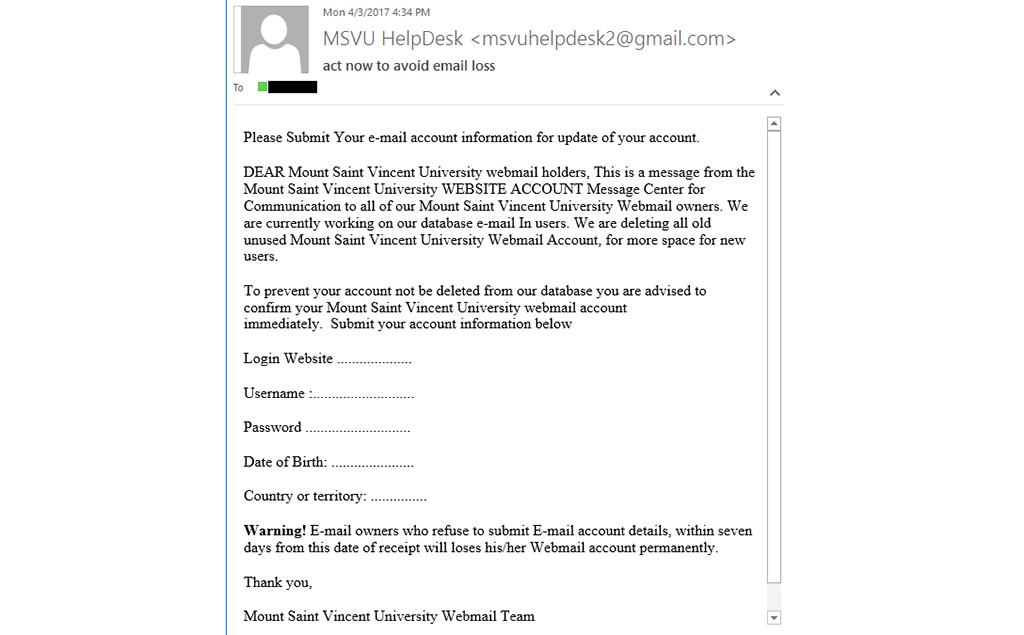
Authentic emails do not require you to input your personal information within the email context. If you receive an unsolicited email from an entity asking you to provide personal information or anything sensitive, be it through a link, attachment, or within the email context itself, you should be suspicious. Most companies do not request your personal information in such a manner.
Treat such emails with caution unless you are 100% sure that the email is genuine with no hidden agenda. Even when you have verified that the given link or attachment points to a legitimate website and everything seems in order, you cannot deny the possibility of a redirection to another malicious website or malware lurking beneath.
8. Emails with an Unfamiliar Greeting or Salutation
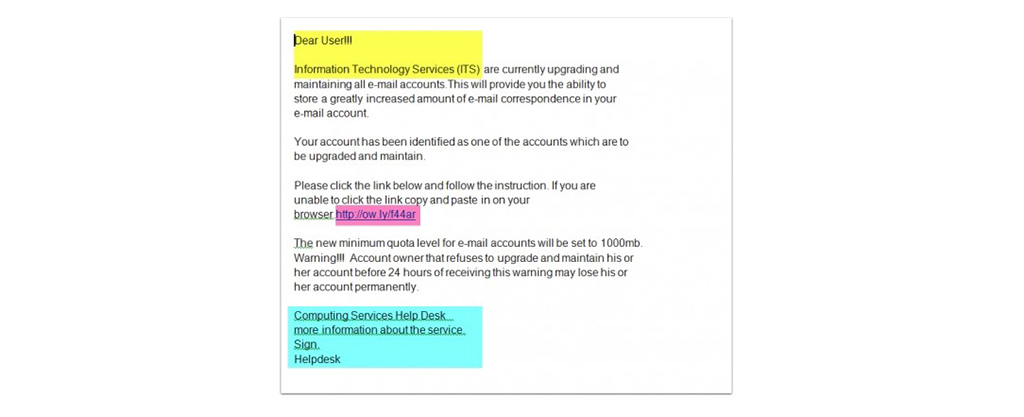
Legitimate companies use your name or formal salutations in their emails. After all, it is the correct email writing etiquette and professional way to go about it. Phishing emails usually begin with generic salutations such as “Hello valuable customer,” “Dear customer,” “Dear account holder,” or “GREETINGS user.”
The most highly suspicious emails usually begin with only “Dear.” Chances are very high that this email is part of a mass phishing attempt.
The above shows an example of an email scam that starts with a generic salutation with three exclamation marks. Authentic emails usually do not use exclamation marks as they go against the proper email writing etiquette. What's more, three of them.
What is Phishing?
Phishing is one type of cyber attack where the hacker conceals the true identity to dupe the victim into believing the hacker enough to complete the desired action. The parallel comes from angling (or fishing).
A bait is placed on a hook and helps to entice a fish to bite. Once the fish bites, the hook sets. The fisherman can then reel it in. In phishing, the email acts as bait. Once you click a link or call a number, the scammer or hacker has you “on the line” and can reel you like a fish on a hook.
Because the victims believe in the authenticity of the emails, they may willingly share valuable confidential information or perform an action that activates malware. Once successful, the hacker can gain anything from network access to financial information.
What is a Common Indicator of a Phishing Attempt?
Phishing emails primarily attempt to impersonate legitimate sources. However, lacking the resources of these institutions, they often include some tell-tale signs. While the emails may seem legitimate, look for minor details, especially when you see a brand you recognize.
For example;
- Spelling mistakes.
- Slight differences in color schemes.
- Alarming email subject lines.
- Urges immediate action.
- Poorly designed email templates.
And more.
How To Protect Yourself From Phishing Attacks
Phishing attacks are rising and becoming more sophisticated. According to a recent report from the Anti-Phishing Working Group, there were 1,270,883 phishing attacks in Q3 of 2022 alone, a record-high number.
Here are five ways to protect yourself from these attacks:
- Avoid clicking email links.
- Always verify the information directly with the source (e.g., your bank).
- Use a password manager to generate and store strong passwords.
- Don't open attachments from unknown senders.
- Use an Internet security app that can monitor your emails.
What To Do if You Suspect Phishing Emails?
If you think you're a target of phishing, do not click on any links in the email. The safest thing to do is mark it as spam or delete it. You can also report phishing emails to the email service provider that you are using.
For example, to report a phishing email in your Gmail account;
- Open the email and click the three dots button next to “Reply.”
- Click “Report phishing.”
Wrapping Up
Socially engineered phishing emails are the scariest and most dangerous. They appear to be relevant and genuine to their targets. Hence, the victims trust the email and obey by carrying out the required task.
The results can range from identity and data theft to network and device infections. It's even worse if you're running a business since it may affect the entire company. But since phishing emails aim at individuals, everyone must be vigilant.
Start by learning to spot the little indicators in a phishing email. There are hidden clues everywhere in phishing emails if you know how to look for them.
Also Read:
- 10 WhatsApp Scams You Need to Avoid
- 12 Amazon Scams to Avoid
- What is HaveIBeenPwned and is it Safe?
- Is AliExpressLegit?