With everything connected to WiFi these days, all the more reason why wireless security is vital in our lives. Almost all smart devices now connect to WiFi networks, whether mobile phone, laptop, or tablet.
Due it the wireless nature of these networks, robust protocols are necessary for protection. As threats evolve, so has WiFi security. From the early days of WEP to new cutting-edge options, we'll cover these, so you know which to choose for your devices.
What Are WiFi Security Protocols?
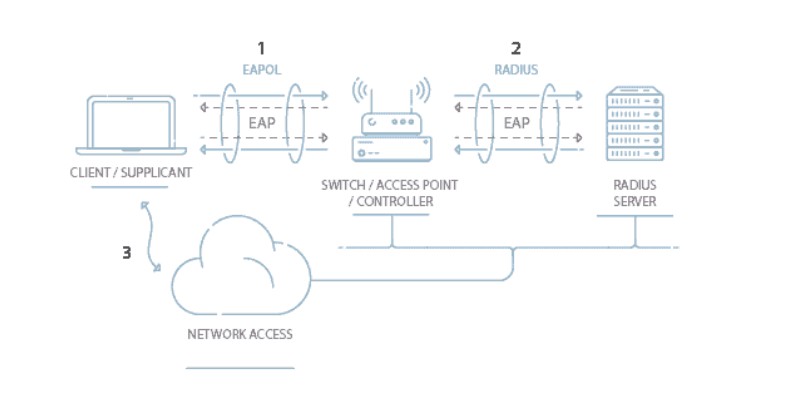
WiFi security protocols help keep your wireless network safe by preventing potential hackers from accessing your device. In comparison with wired networks, wireless networks are less secure. That's why we design WiFi security protocols – to protect data and communications carried across wireless networks.
In simpler terms, hackers can quickly obtain all of our passwords without encryption. These days, hackers can use various software variants to gain access to any network within just a few clicks. Without encryption, they can easily steal sensitive information like login credentials.
How WiFi Security Works
The Wireless Alliance is a non-profit organization that owns the official trademark of WiFi. They created WiFi security protocols, which are authentication protocols made to protect wireless security with encryption.
Over the years, we've seen the creation of various WiFi security protocols. The current ones are WEP, WPA, WPA2, and WPA3. These use a combination of techniques to increase security. For example, cryptographic keys that randomize data.
Comparing WEP, WPA, WPA2, and WPA3 WiFi Security Protocols
WiFi security protocols are the primary components that determine the level of protection of your home or office network. There are several types of WiFi security for home and commercial users. These types include WEP, WPA, WPA2, and WPA3.
Wired Equivalent Privacy (WEP)
WEP was the first WiFi security protocol created (and getting updates) from the late 1990s up to 2004. It uses the most basic level of encryption (64/128-bit). Aside from the weak encryption, WEP is not an easy security protocol to use as the configuration was difficult.
The least stable WiFi security protocol is WEP, which was discontinued in 2004 by the WiFi Alliance.
WiFi Protected Access (WPA)
WPA, developed in 2003, uses 128-/256-bit encryption, which is known to be stronger. Despite being a step further than WEP, it still isn't as comprehensive enough to ensure proper security. Nonetheless, regarding device compatibility, WPA is compatible with most of the devices in the market.
This basic form of security uses a password shared between the router and your devices. This password can be as simple as “12345678” or “password.” If you choose this option, you should ensure that your password is at least eight characters long and contains both letters and numbers.
WiFi Protected Access 2 (WPA2)
WPA2, developed in 2004, is where they took a step further to enhance the security measures by implementing AES (Advanced Encryption System), which does a much better job at encrypting data. Thus, only those with the password to your network can access the data.
However, WPA2 does come with flaws. The access points with WPA2 enabled may still be vulnerable to attacks made through WEP. Hence, it would help if you disabled WEP on your access points.
Another thing to note is that the WPA2 protocol is vulnerable to attacks by Key Reinstallation Attacks (KRACK). Thankfully, WPA3 managed to eliminate the risk of KRACK attacks.
WiFi Protected Access 3 (WPA3)
WPA3 was officially certified in July 2022. It is a much-advanced WiFi security protocol as it implements the Protected Management Frames that prevent forging and eavesdropping. This WiFi protocol also uses 192-bit encryption for businesses and 128-bit encryption for personal use. These are higher than WEP, WPA and WPA2 combined.
This protocol is beneficial for public networks as it automatically encrypts the connection without needing login credentials. WPA3 also uses Simultaneous Authentication of Equals (SAE), which eliminates any repeated use of encryption keys. It ensures that you use a new code through each interaction.
SAE also prevents brute force attacks as they will notify of multiple connection attempts. On top of that, “forward secrecy” is beneficial to stopping hacks that are already present in networks. Saved or captured data can easily be made redundant.
Choosing the Best WiFi Security Type for Your Devices
All modern connected devices need WiFi security. Whether you are a home user or a small business owner, these protocols help aid communication and protect our devices and data. Yet, with so many protocols available, the dilemma becomes how to choose the best WiFi security type for your devices.
When to Choose WPA
You're using older software or a device that isn't compatible with the newer security protocols. It would be best if you didn't use WPA for business purposes as it doesn't offer maximum security. This type of security isn't good enough for protecting critical data like banking information or passwords, but it will help keep nosy neighbors from snooping on your internet connection.
When to Choose WPA2
WPA2 emerged thanks to flaws seen in WEP and WPA. Because of these issues, WPA2 has become a standard for most WiFi devices sold today. It's the current defacto standard for home and business devices. However, it might not work well for old devices as it requires more processing power.
When to Choose WPA3
Use WPA3 if you're always in public places such as restaurants or coffee shops. It's also suitable for businesses with plenty of private data as the security features are pretty tight and are considered the safest (and fastest!) among the other two.
The only downside is that not all devices support WPA3. Most old devices aren't compatible with WPA3.
Why WiFi Security is Important
1. Preventing Man-in-the-middle Attacks
A common cyber attack would be a hacker penetrating a private network by acting as an access point to capture login details. They will pretend to be a trusted network (such as a WiFi network) and lure the victims into connecting and entering the login details.
2. Avoiding Packet Sniffers
Packet sniffers are low-level applications that monitor network traffic. Hackers can use these applications to gather and examine all data being transferred throughout a network. When the data is used for unethical purposes, it could potentially destroy a network.
3. Staying Clear of Brute Force Attacks
Brute force attacks are common. It involves submitting various passwords to guess the right one. These days, there are various tools a hacker can use to speed up the process and get the right one.
4. Preventing Downtime or Lag
Network connection bandwidth is always finite. Due to bandwidth limitations, occasional traffic surges can cause instability. Network security helps to minimize downtime by monitoring connections for suspicious activity.
5. Avoiding the Risk of Cyber-vandalism
For businesses, hackers can enter the system and plant wrong information, causing problems to the entire company. The intellectual property of a company is one of the most important aspects.
The company's entire network might have to go through downtime to save themselves back from the hacking incident. This also leads to potential revenue loss, as productivity will suffer for as long as the network is erratic or unavailable.
Other Ways to Increase Your WiFi Security
Other than using WiFi security protocols, here are different ways you can ensure your WiFi is properly secured:
1. Create and Use Strong Passwords
Using the most robust password that you can think of is crucial to prevent anyone from ever guessing it. The guidelines to create a strong password would be to make it at least 16 characters and use a broad mixture of lowercase & uppercase letters, special characters, and numbers.
You can consider using a password manager such as LastPass to keep track of all your different passwords. Some password managers even generate strong passwords for you.
2. Use Media Access Control Addresses
One of the basic security measures would be to use Media Access Control (MAC) addresses which create a unique number or code for every individual using the network.
3. Use a VPN (Virtual Private Network)
A Virtual Private Network (VPN) is one of the most secure methods to protect your internet connection. Since it acts as a middleman between the internet and your device, it hides your activity so that no one can track it (including online advertisers).
There are both free and paid versions of VPN. HideMyTraffic curates lists of the Best VPNs available for various use cases.
4. Install Security Applications
You can consider installing security software that provides WiFi security for your devices connected to WiFi, such as access points, routers, and switches. Most of this security software tends to have other products that can provide more security, such as antivirus software.
5. Rename Your Network and Routers
Most of the devices and networks come with a default username and password. The default information is the same across all devices and, therefore, public records, making it easy for hackers to access.
As for the network names, usually, it will be the brand and model number of the router. Hence, hackers will quickly discover how you set up your WiFi network.
Conclusion: WiFi Security is Essential
With this guide, you will better understand the different WiFi encryption types and be better equipped to pick which type is best for your use. WiFi security will stay a hot topic of discussion between now and the foreseeable future.
The WiFi security protocol known as WPA2 is currently the best to protect your WiFi network and data. However, due to its age and teething problems with WPA3, it wouldn't be surprising to see it replaced as WPA3 issues get resolved.