Virtual Private Networks (VPNs) can be pretty technical. While the concept is relatively simple, the technical jargon used in these tools can confuse many. One area that needs to be clearly understood is Data Encryption since this helps keep your information safe.
What is Data Encryption
Data Encryption is converting data to an unintelligible form called ciphertext. The ciphertext looks like a meaningless string of characters and numbers. Only those authorized to access the encrypted data can decrypt it, which converts it back into its original form so that it can be understood.
How Data Encryption Works
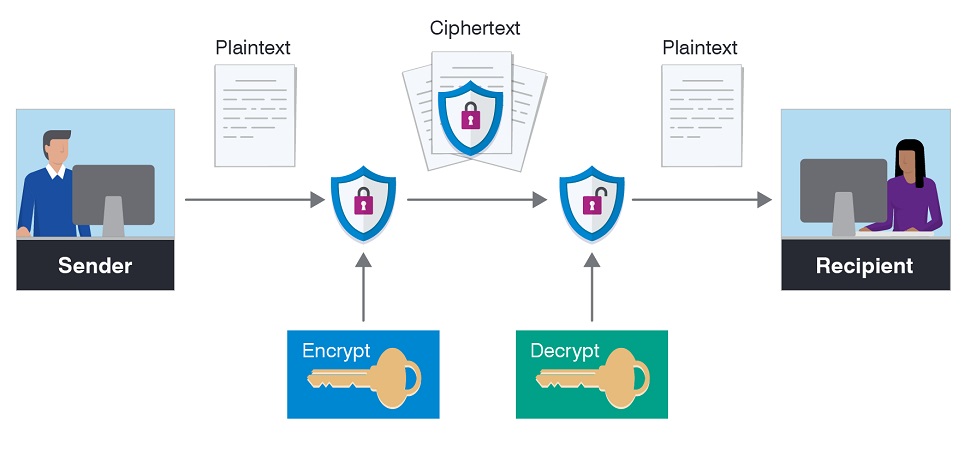
Data Encryption is a two-way process. The data is encrypted with an encryption key, turning it into ciphertext. This ciphertext can be decrypted only with the correct key, turning it into usable data again.
There are two main types of encryption: Symmetric Key and Asymmetric Key.
Symmetric Key Encryption
Symmetric Key Encryption is a system where the sender and receiver of a message share a common key used to encrypt and decrypt the message. Data encrypted with a Symmetric Key can only be decrypted using that same Symmetric Key.
For example: when you leave your house, you lock your door with a single key. Anyone possessing the same key can unlock the door and enter your house.
Asymmetric Key Encryption
Asymmetric Keys use two keys at once, a Private Key and a Public Key. Anything encrypted with the public key can only be decrypted by the Private Key and vice versa. The Private Key is kept secret, while the Public Key may be widely distributed via a publicly accessible repository or directory.
For example: when you want to send someone sensitive information, you encrypt it using their public key. Once encrypted, only the receiver can decrypt it using the corresponding private key, then read the contents.
Data Encryption Algorithms – How Data is Coded
A Data Encryption Algorithm is a complex mathematical function that turns plaintext into ciphertext. It takes a variable-length string of plaintext and transforms it through a series of complicated operations into another ciphertext string of fixed length.
It's important to note that the transformation is reversible — it can be undone using the same or a different key.
There are many different types of Data Encryption algorithms, but a few examples of data encryption algorithms include:
Data Encryption Standard
In the 1970s, experts developed a symmetric block cipher called Data Encryption Standard (DES). It was used for years and was eventually considered too weak for ongoing use since its 56-bit key length can be broken using brute force attacks. The US government replaced this algorithm with Advanced Encryption Standard (AES).
Advanced Encryption Standard
Advanced Encryption Standard (AES) is the most popular symmetric-key algorithm. The National Institute of Standards and Technology (NIST) adopted it as FIPS 197 in November 2001 after a five-year standardization process.
AES replaced DES on December 31, 2001, as the standard symmetric-key encryption algorithm. Today, you can encounter AES in WiFi routers, mobile devices, and financial products such as PIN pads and credit cards.
Triple DES
The Triple Data Encryption (3DES) algorithm created by IBM in 1998 protects sensitive information. Due to its high level of security, the US government uses 3DESto secure classified information. However, it is considered less desirable than AES due to its slow speed and small key size.
3DES is also susceptible to brute force attacks using computers, which makes it unsuitable for many commercial uses today.
RSA
Invented more than 30 years ago, RSA is still widely used today, despite some severe flaws discovered in 1994. These flaws made it possible to decrypt encrypted messages quickly and effectively, but since then, RSA has been strengthened even further and is now considered very secure.
The RSA algorithm uses two huge prime numbers (100+ digits long) for its security. A prime number is a whole number greater than 1 whose only factors are 1 and itself. The first step in encrypting data is to generate these two randomly selected prime numbers and multiply them to create the public key modulus.
Blowfish
The Blowfish algorithm is a symmetric block cipher designed in 1993 by Bruce Schneier as an alternative to existing encryption algorithms. It was designed to be small, fast, and flexible. It is also unpatented and license-free.
Blowfish has a 64-bit block size and a variable key length from 32 bits up to 448 bits.
In practice, Blowfish has been found to be one of the fastest available encryption algorithms, making it very well suited for use in real-time systems such as disk encryption programs or Internet traffic encryption programs.
Twofish
The Twofish encryption algorithm was one of the five finalists in the AES contest and is a speedy, free and open-source symmetric key block cipher. It is used by some VPNs, software programs, and hardware devices to encrypt data.
Twofish is highly secure and, so far, resistant to all known attacks. It has a large block and key size and can be efficient on many platforms. The name “Twofish” comes from its 128-bit block size, 128-bit key size, and 16 rounds.
RC4 Encryption
RC4 is a stream cipher — which means that it encrypts a single bit of plaintext at a time. Stream ciphers are faster than block ciphers, but they require more memory and are less secure because they use fewer complex mathematical functions.
RC4 was created in 1987 and made public in 1994. It quickly became one of the most popular encryption methods because it was easy to implement and worked well with hardware and software. Today, just about every web browser uses RC4 as its default encryption algorithm to transfer sensitive data securely over SSL (Secure Sockets Layer) connections.
Encryption Key Bitrate
Encryption Key bitrate size is a measure of the strength of your data's encryption. There are four common Encryption Key Bitrate sizes and they are 56 bits, 64 bits, 128 bits, and 256 bits. Lower or smaller sizes are considered weaker and will be easier for hackers to break.
The strength of an encryption key changes or updates over time and is often reliant on other factors. The main contributor to this is the nature of mathematical algorithms, which change over time due to advances in technology, additions to system resources, etc.
What is End-to-end Encrypted Data?
End-to-end encryption is a method of data transmission that prevents third parties from accessing the information being transmitted. The data is encrypted on one end and then decrypted on the other. It also means that only the sender and recipient have access to the information.
In some cases, it's possible to encrypt data at multiple points along its path — but this isn't required for it to be considered end-to-end encryption.
While end-to-end encrypted data can only be viewed by its intended recipient, it can be intercepted in transit by a third party. The critical difference with end-to-end encryption is that even if an unauthorized person intercepts the data, they won't be able to read it — they'll only see gibberish.
End-to-end encryption has become a must-have feature for messaging apps, social media, and other online platforms, particularly after revelations about government surveillance programs were made public by Edward Snowden in 2013.
Benefits of Data Encryption
Data Encryption is becoming more common as companies store more and more information on servers, in the cloud, and on mobile devices. This widely used method of securing data is not as straightforward as it may appear on the surface. Some of the critical benefits of encryption include:
Security: Encryption protects your data from unauthorized access by rendering it useless to anyone who does not have the key for decoding it
Compliance: Data Encryption is one of the ways that companies can meet the requirements of various regulations such as HIPAA, FISMA, and PCI DSS.
Control: Data Encryption helps organizations maintain control over their data assets, regardless of where they are stored
Transparency: Data Encryption enables organizations to protect sensitive information without impeding business processes.
Data Encryption provides confidentiality, integrity, and authenticity to data stored or transmitted over a network. Using data encryption, only authorized parties have access to the content of an encrypted message.