Suspicious app downloads can compromise your data, drain your battery, or even cost you money. That's a severe problem since mobile apps have become integral to our daily lives. From banking to entertainment, we rely on various apps for many things.
However, there's also an increase in malicious software disguised as legitimate applications. These deceptive applications pose threats that can ruin your day. Sadly, telling the malware from legitimate apps can also be challenging.
To help you navigate the app world safely, here are 10 tips to avoid downloading suspicious apps:
- Check the Developer/Publisher
- Read Reviews
- Check Permissions
- Avoid Third-party App Stores
- Update Your Operating System
- Look at the Download Count
- Check for a Secure Connection
- Use Mobile Security Software
- Be Wary of Clone Apps
- Trust Your Instincts
To protect against suspicious apps:
- Always download apps from trusted sources, such as official app stores.
- Regularly update your device's operating system and apps.
- Read app reviews and check permissions before installing.
- Use a reputable mobile security solution to scan for and remove malicious apps.
1. Check the Developer/Publisher
The developer behind an app can often indicate its legitimacy. Reputable developers maintain a standard of trust and security. Established developers have a reputation to uphold, making them less likely to jeopardize user trust.
On the other hand, malicious entities might create one-off developer profiles to push harmful apps.
What you can do: Investigate the developer's history. Have they produced other apps? What do reviews of those apps say? A consistent track record of positive feedback can be reassuring.
2. Read User Reviews
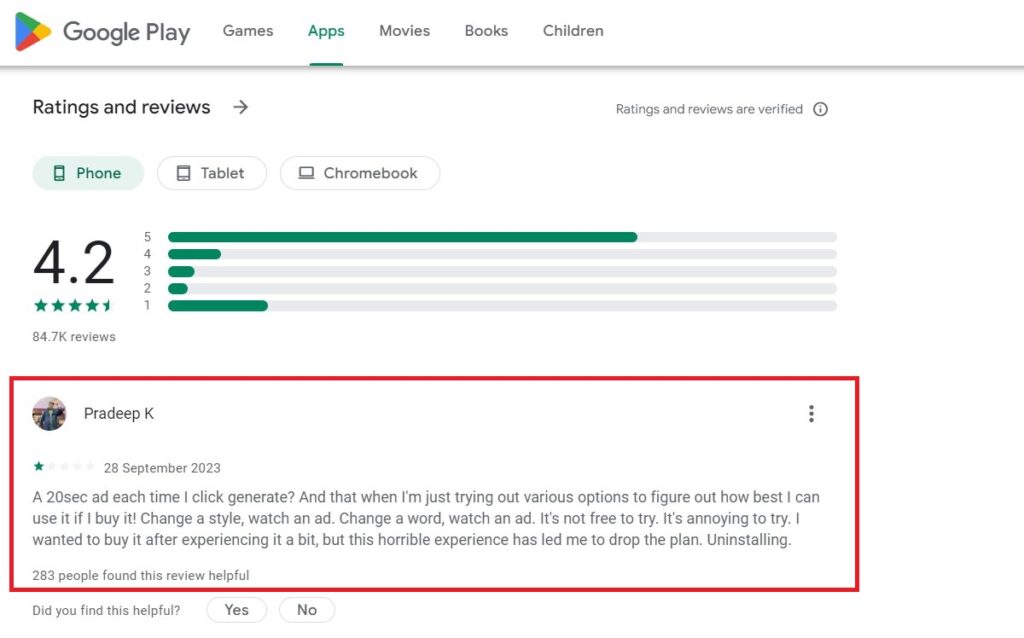
Reviews are firsthand accounts of user experiences, offering insights into potential issues or benefits. While developers can sometimes plant positive reviews, many similar complaints can indicate underlying issues. Reviews can also highlight features (or pitfalls) not mentioned in the app description.
What you can do: Look for patterns in reviews. Are users consistently praising or complaining about specific features or behaviors? Such patterns can guide your download decision.
3. Check Permissions The App Wants
Permissions act as gateways, granting apps access to various device functionalities and data. While these permissions are often necessary for apps to function correctly, they can also be potential vulnerabilities if misused.
Understanding and managing app permissions is crucial for maintaining device functionality and personal privacy.
Excessive permissions can be a sign of underlying malicious intent or data mining.
The deeper dive: Some apps might request permissions that aren't necessary for their function, which can be a red flag.
For instance, a game asking for access to your contacts might be overreaching.
What you can do: Scrutinize the permissions list. If you're unsure why an app needs a particular permission, research it or contact the developer for clarification.
4. Avoid Third-party App Stores
Official app stores have rigorous vetting processes, ensuring higher app security. Third-party stores might have less stringent checks, making them more susceptible to hosting malicious apps. They might offer tempting apps or deals, but the risks can outweigh the benefits.
What you can do: Prioritize downloading from official sources (such as the Google Play Store or Apple App Store). If you must use a third-party store, ensure it has a solid reputation for security.
5. Update Your Operating System
OS updates often come with security enhancements that protect against new threats. Just as apps evolve, so do the threats against them. OS developers regularly release updates to counteract these threats and fix vulnerabilities.
What you can do: Enable automatic updates for your OS or regularly check for and install updates manually.
6. Look at the Download Count
A download count might appear as just a number. However, it can significantly indicate an app's credibility and popularity. However, like all metrics, it's essential to interpret it discerningly.
A high download count can indicate an app's popularity and, often, its reliability. However, some malicious apps use tactics to inflate their download numbers or might become popular before being identified as harmful.
What you can do: Use download counts as a preliminary gauge. Ensure you combine this with other checks like;
- User Reviews
- Update Frequency
- Developer Reputation
7. Check for a Secure Connection
Secure connections reduce the risk of data interception. HTTPS ensures data between your device and the server is encrypted. This is especially crucial if you're providing personal or financial information.
What you can do: Always check for “https://” in the URL when downloading from a website. Avoid downloading apps from sites with unsecured connections.
8. Use Mobile Security Software

Security software offers real-time protection against threats. These tools can identify and block known malicious software, scan apps for suspicious behavior, and even offer added features like anti-phishing.
Mobile security software isn't just about virus scans. Modern solutions offer a suite of features designed to protect various facets of your digital life:
- Real-time Scanning: Continuously monitors your device for threats, ensuring that any new app you install is immediately checked.
- Anti-phishing: Detects and blocks phishing attempts, and fraudulent attempts to obtain sensitive information, often through deceptive websites or emails.
- Firewall: Monitors data access to and from your device, blocking unauthorized or malicious access attempts.
- App Privacy Check: Reviews the permissions of your installed apps, highlighting those that might be overreaching in their data access requests.
- Anti-theft Features: You can locate, lock, or wipe your device remotely if lost or stolen.
What you can do: Choose a reputable mobile security app, keep it updated, and run regular scans.
9. Be Wary of Clone Apps
One of the most deceptive threats users face is the presence of clone apps. These applications closely mimic popular, legitimate apps' appearance, name, and functionality but often come with hidden malicious intentions.
The primary motive behind creating clone apps is to deceive you. Popular apps have a proven track record of user interest and demand. By mimicking these apps, malicious developers can tap into an existing user base, tricking them into downloading their counterfeit version.
Once downloaded, these clone apps can serve various nefarious purposes, from displaying intrusive ads to stealing user data or introducing malware.
What you can do: Double-check all details before downloading, especially if an app's popularity seems sudden or unexpected.
10. Trust Your Instincts
Your intuition can be a powerful tool in identifying potential red flags. Sometimes, something might feel off even if everything seems to check out. This gut feeling can be based on subtle cues or patterns you've observed in the past.
What you can do: If you're ever in doubt, it's better to hold off on a download. Take some time to do more research or look for alternatives.
What Are Suspicious Apps?
Suspicious apps refer to software applications that may exhibit behaviors or characteristics indicative of malicious intent. These apps generally act to compromise the security, privacy, or functionality of a device or system. Here are some features and behaviors that can make an app suspicious:
- Unauthorized Data Access
- Excessive Permissions
- Background Activities
- Unusual Data Usage:
- Unwanted Advertisements
- Unsolicited Installation
- Unexpected Charges
- Behavior Changes
Every time we download an app, we grant it a level of trust and access. In the ideal scenario, this trust is reciprocated with genuine service. However, in the shadows lurk malicious entities eager to exploit this trust. Suspicious apps can be gateways for a myriad of threats.
The risks are manifold, from data theft, where personal information is stolen and sold or used for identity theft, to malware that can hijack device functionalities. Financial losses are another concern, with some rogue apps making unauthorized transactions or subscriptions.
But it's not just about the tangible threats. There's also the psychological impact. Imagine the distress of finding personal photos leaked online or the anxiety of knowing someone might be monitoring your every move through a compromised app. Such violations can have lasting emotional repercussions, emphasizing the importance of app safety.
Ensuring the apps we download are safe is akin to ensuring our digital homes are secure. Just as we wouldn't allow a stranger with dubious intentions into our homes, we shouldn't let suspicious apps into our devices.
Increase Your Digital privacy and Security With a VPN

Although a Virtual Private Network (VPN) is limited in protecting you from suspicious app downloads, these handy tools significantly improve your digital privacy and security.
A VPN creates a secure, encrypted connection between your device and the internet. It's primarily used to maintain privacy, bypass geo-restrictions, and protect data from potential eavesdroppers, especially on unsecured networks.
The two most important features of a VPN are;
Encryption: A VPN encrypts your internet connection, ensuring that the data you send and receive is private and secure. This is especially useful when using public Wi-Fi networks, which are often less secure and more susceptible to eavesdropping.
IP Masking: By routing your connection through a server in a location of your choice, a VPN masks your actual IP address. This not only helps in maintaining anonymity but also allows users to bypass geo-restrictions.
Final Thoughts
Navigating the security of mobile applications requires a blend of enthusiasm for innovation and a healthy dose of caution. As the potential of apps continues to expand, so too do the risks associated with malicious entities seeking to exploit us.
While tools like VPNs offer layers of protection in specific scenarios, they are but one piece of the broader security puzzle. We must all adopt a holistic approach to digital safety, combining technological solutions with informed habits and vigilance.
By staying updated, regularly reviewing app permissions, and being discerning about downloads, we can harness the immense benefits of mobile apps without compromising our digital well-being.