A VPN works by passing your connection through a secure server before accessing the sites you want on the Internet. In most cases, the VPN will also encrypt your data before sending it through the connection. This helps keep your information both private and secure.
Normally, when you type the URL of a website you want to visit into your browser address bar, you will be connected to that site directly. Using a VPN service modifies this process a little bit so it may slow your connection speed.
Connecting to a VPN Server
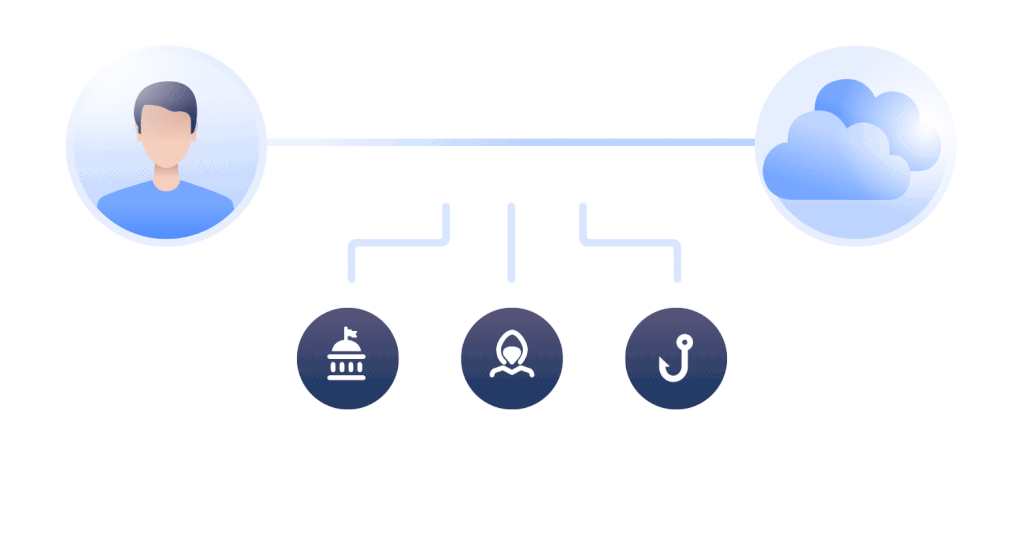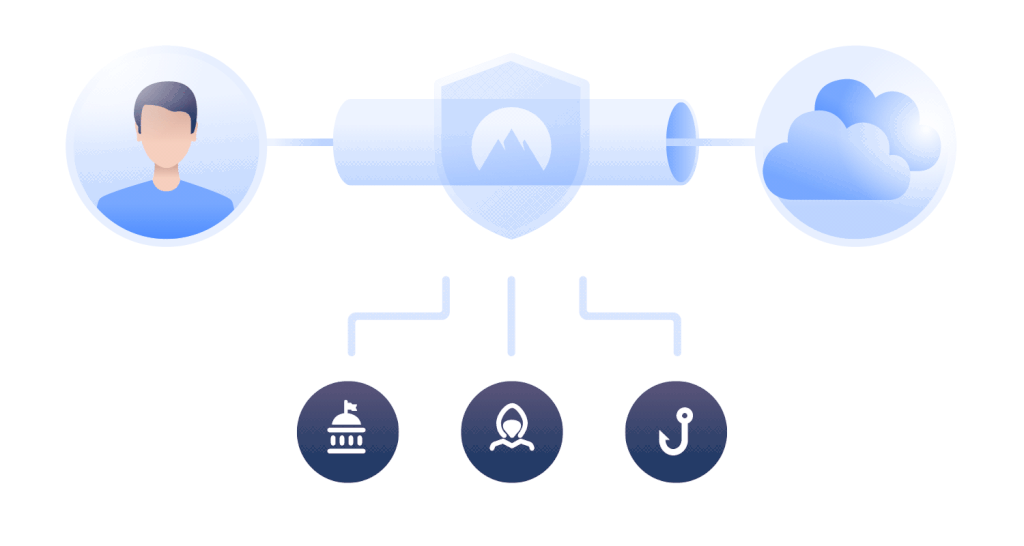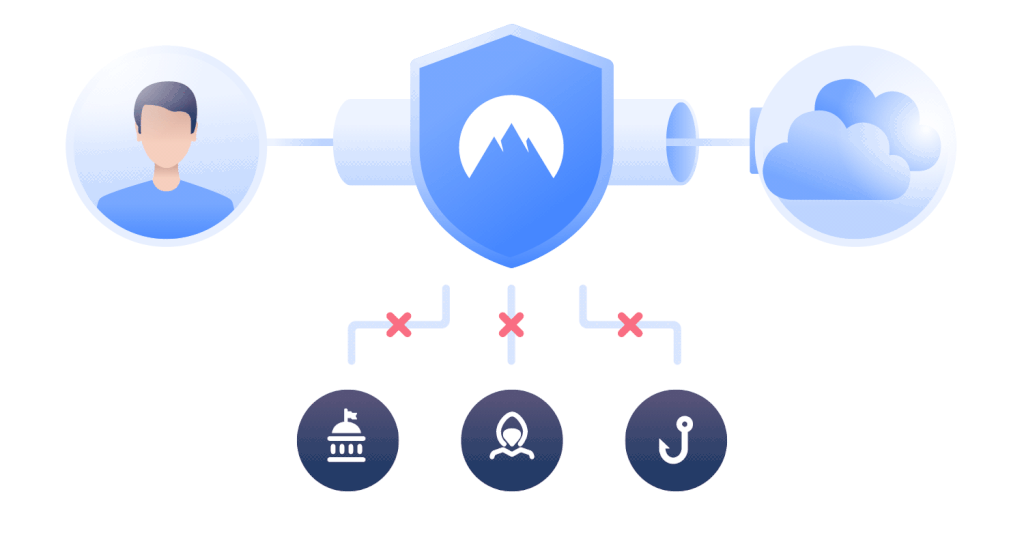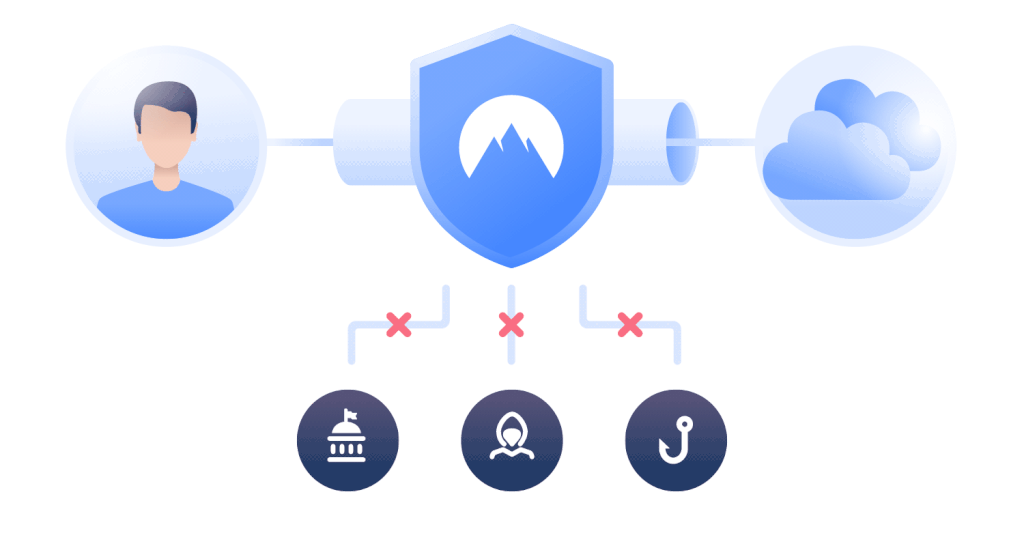
There are many ways a VPN can work. The easiest and most direct method is to make use of an application provided by the service. Installing and launching this application, then choosing a server to connect to, is typically all it takes to work.
However, most VPNs will only develop applications for mainstream platforms such as Windows, Linux, Android, or iOS. For others, manual connection methods may need to be used. How this works depends on what devices you are trying to connect (for example, connecting a VPN on routers).
Once connected, when you type a URL in your browser address bar the request will be routed through the VPN server. The VPN server acts as the ‘public face’ of your connection. This means that anything monitoring a connection will assume it came from the VPN server. The process helps to achieve a few things, such as masking your origin IP.
For example, if you connect to a US-based VPN server, any other site or service you connect to will assume that you are physically in the United States. You can choose to connect through any country in the world if your VPN service provider has a server in that location.
If you are not using a VPN, your ISP will know everything that you do online, right down to the exact time you do it at. A VPN will help mask your search history since anything you do online will be associated with the VPN server, not your own IP address. VPNs keep your online activity private.
VPN Protocols and Encryption
There are two main components of a VPN connection, the connection protocol, and encryption. The connection protocol helps determine how two systems (in this case, your computer or device and the VPN server) communicate.
The encryption protocol determines what type and level of encryption is applied to any data that is travelling along the tunnel established by the communication protocol. The higher the encryption the safer your data will be.
Communication Protocols
So far there have been five main protocols which VPN services have been using:
OpenVPN –Is an open source protocol which is extremely popular today. It can be used by almost any platforms on most devices and is able to support high levels of encryption. Although in the past criticized for being quite slow, updates to the protocol have made it much more viable than ever.
L2TP/IPSec – Layer 2 Tunnel Protocol is the protocol which replaced PPTP. There is no native encryption in this protocol which is where IPSec comes in. IPSec offers extremely high levels of encryption and the combination of L2TP/IPSec is both fast and potent.
SSTP –This is another strongly encrypted protocol that comes along as an option on many VPN services today. Unfortunately, it is proprietary to Microsoft and as such has not been audited for security by external parties.
IKEv2 –Owned by Microsoft and Cisco, Internet Key Exchange version 2 is also usually combined with IPSec for better security. It is highly popular in mobile usage because of its strong capabilities in handling reconnects such as during the period of travel between coverage of cell phone base units.
PPTP –One of the oldest connection protocols around, Point-to-Point Tunneling Protocol is one of the oldest VPN protocols. It is still in use in some places, but most services have long upgraded to faster and more secure protocols.
PPTP was introduced way back in 1995. It was integrated with Windows 95, designed to work with dial-up connections. At the time, it was extremely useful.
But the VPN technology has progressed, and PPTP is no longer secure. Governments and criminals cracked PPTP encryption long ago, making any data sent using the protocol unsecure.
However, it is not quite dead… yet. You see, some people find PPTP gives the best connection speeds, precisely due to the lack of security features (when compared to modern protocols). As such, it still sees use for users simply wanting to watch Netflix from a different location.
Encryption
The communication protocol plays a role in securing the connection between you and the VPN server. However, that is only half of the solution. Encryption helps increase security further by scrambling data before sending it though.
Think of it as locking a box with a digital code before sending it to someone else by registered mail. Even if the box is stolen while on the way to its destination, the thief will not be able to get what is inside the box without knowing the code.
Most top VPN service providers use the Advanced Encryption Standard (AES). This is the most secure encryption standard currently available and is used by military forces in various scenarios. There are varying levels of AES encryption such as 128-bit or 256-bit.
The higher the encryptions standard, the more difficult it is to break. To date, there have been no known instances of 256-bit AES being broken.
Some VPN service providers allow users to adjust encryption levels because encryption can affect VPN speed. Since encryption and decryption is done on the device, lower quality hardware can sometimes struggle to keep up.
The important thing to remember is that by lowering the encryption level, you are potentially compromising on your data security.
Pros and Cons of VPN Protocols
- OpenVPN: Open source, offers strongest encryption, suitable for all activities, if a little slow at times
- L2TP/IPSec: Widely used protocol, good speeds, but easily blocked due to reliance on single port
- SSTP: Good security, difficult to block and detect
- IKEv2: Fast, mobile friendly, with several open source implementations. Unfortunately, this protocol has been potentially undermined by the NSA.
- PPTP: Fast, widely supported, but full of security holes, only use for streaming and basic web browsing.
In more recent times, a new protocol has emerged, and has been undergoing extensive development. WireGuard seems to be the future of VPN technology. There are currently only a handful of VPN service providers which offer either full or partial implementations of WireGuard such as NordVPN and TorGuard.
Final Thoughts
As you can see, VPN services make use of two core elements. However, there is much more information to cover to fully understand them. To see how beneficial VPNs are and to go over the rest of this information, read my VPN Guide.