Hey there, future Kali Linux user! Excited to step into the world of digital security? You're in the right place. This guide is your ticket to understanding and using Kali Linux, a powerhouse in digital security.
Ever heard of Kali Linux? If not, no worries. We're here to break it down for you. Kali Linux is a potent tool, a distribution crafted with digital security, ethical hacking, and penetration testing in mind. It's a must-have skill for anyone dipping their toes into cybersecurity.
In this guide, we will unravel the mystery of Kali Linux. We'll walk you through everything from the installation process to its practical applications. And don't worry if you're a beginner. We've got you covered with easy-to-understand explanations and step-by-step instructions.
So, are you ready to master Kali Linux? Let's jump right in!
- What is Kali Linux?
- Advantages of Using Kali Linux
- What You Can Do With Kali Linux
- Kali Linux Installation Methods
- Installing Kali Linux on VMWare Player
- Navigating the Kali Linux Interface
- Recommended Kali Linux Tools
- Troubleshooting Common Kali Linux Issues
- Kali Linux User Communities and Forums
- Comparing Kali Linux vs Ubuntu
- Kali Linux: A Journey Towards Privacy and Protection
What is Kali Linux?
Kali Linux is a powerful distribution designed specifically for digital security. This unique Linux distribution plays a crucial role in digital security. For example, experts use it to identify vulnerabilities in systems. These vulnerabilities can then be quickly patched to improve system security.
It also plays a crucial role in ethical hacking. Ethical hackers, also known as white hat hackers, use the same techniques as malicious hackers. But they use their skills to improve the system's security, not for personal gain.
It's also used for forensic work. Investigators use it after a cyber attack. They can trace the source of the attack. They can understand the attacker's methods. This information can be used to prevent future attacks.
Advantages of Using Kali Linux
You might be wondering why you should consider choosing this particular distribution. After all, there are many Linux distributions out there. Ubuntu, Fedora, and Debian are all popular choices. But this Linux distribution holds a special place, especially for digital security enthusiasts.
Firstly, Kali Linux is designed for ethical hacking and penetration testing. It offers a collection of the best security and hacking tools. It includes over 600 preinstalled penetration-testing programs. Tools like Wireshark, Metasploit, Nmap, and more are all at your fingertips.
Secondly, Kali Linux is regularly updated. The team at Offensive Security constantly adds new tools and features. This ensures you always have the latest and greatest tools for digital security.
Thirdly, there's a large and active community. There are plenty of online forums, tutorials, and resources. If you're stuck on a problem, chances are someone else has faced it and found a solution.
Finally, it's free and open-source. You can modify and customize it. It's perfect for learning and experimenting.
But remember, with great power comes great responsibility. Kali Linux should never be used for illegal activities. Always obtain proper permissions before testing any systems.
What You Can Do With Kali Linux
Kali Linux is more than just a collection of tools. It's a versatile platform that can be used in various practical applications. Here are a few ways you can use it in real-world scenarios:
Become a Network Detective
One of the primary uses is for network analysis. Tools like Wireshark and Nmap allow you to monitor network traffic, identify open ports, detect network vulnerabilities, and much more. This can be incredibly useful for identifying potential security risks and taking steps to mitigate them.
Test Your Defenses with Penetration Testing
Kali Linux is a go-to platform for penetration testing. With tools like Metasploit and Burp Suite, you can simulate real-world attacks on your network or web applications. This can help you identify vulnerabilities before malicious actors can exploit them.
Solve Digital Mysteries with Forensics
This unique OS includes tools for digital forensics. These tools can help you recover lost data, investigate potential cybercrimes, or analyze a system after a security incident. Tools like Autopsy and Sleuth Kit are explicitly designed for this purpose.
Put Your Passwords to the Test
Tools like John the Ripper and Hydra can be used to test the strength of your passwords. This can help you ensure that your passwords are robust enough to withstand attempts at cracking.
Assess Your Wireless Fortress
Kali Linux includes tools like Aircrack-ng and Reaver, which can be used to assess the security of wireless networks. This can be particularly useful if you're setting up a new wireless network or trying to improve the security of an existing one.
Kali Linux Installation Methods
The most common method for installation is by downloading the ISO (disk image) file from the official website. This method gives you full control over the installation process and allows you to customize various settings.
With the ISO file in hand, there are various ways that you can install Kali Linux;
- On a fresh device.
- Dual booting Kali Linux with other operating systems.
- Using a virtualization tool like VMWare Player.
Most of us won't have spare machines lying around, and I don't recommend dual booting for new users. There's a chance things can go wrong. Virtualization is the safest bet, so I'll provide a guide for installation on a Virtual machine (VM).
Installing Kali Linux on VMWare Player
A VM provides a convenient and safe way to run Kali Linux on your computer without changing your existing operating system. There are several popular VM, including VirtualBox and VMWare Player.
For this example, I'll provide a step-by-step guide to installing it with VMWare Player:
Step 1. Download and Install VMWare Player
VMware Workstation Player (formerly VMware Player) is free. VMware offers both a free and paid version called VMware Workstation Pro, which includes additional features and capabilities. The free VMware Workstation Player provides enough basic virtualization capabilities for home users.
If you haven't already, download and install VMWare Workstation Player from the official VMWare website. Once the download is complete, launch the installer and follow the installation instructions provided by VMWare.
Step 2. Download and Import the Pre-built Image

Visit the official Kali Linux official Virtualbox image page and download the pre-built image for VMware Player. Make sure to choose the appropriate version and architecture.
Once downloaded, launch VMware Player and click the “Open a Virtual Machine” option. Browse to the location where you downloaded the pre-built image, select it, and click “Open.” VMware Player will display the import options for the pre-built image.
Customize the virtual machine settings according to your preferences, such as the name, location, and disk size. Ensure the guest operating system is set to “Linux,” and the version matches your downloaded image. Click “Import” to proceed.
Once the import is complete, you'll see the imported virtual machine listed in VMware Player. Select the virtual machine and click “Play virtual machine” to start it.
Step 3. Complete the Initial Configuration
Follow the on-screen instructions to complete the initial configuration. This may include setting up language preferences, time zone, keyboard layout, and creating a user account with a password.
Step 4. Explore Kali Linux on VMware Player
After the initial configuration, you'll be logged into the OS on VMware Player. Take some time to explore the interface, access the pre-installed tools, and familiarize yourself with the environment.
Navigating the Kali Linux Interface
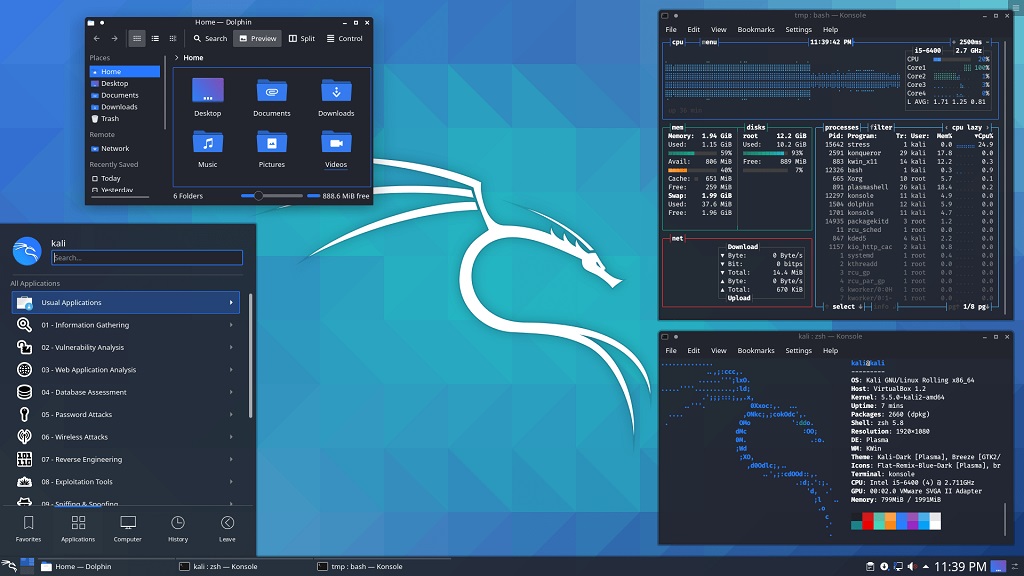
Once the installation is done, it's time to familiarize yourself with the interface. Here's a quick guide to help you get started.
The Kali Desktop Environment
You get the Xfce desktop environment by default. It's lightweight and easy to use. You'll find icons for your home folder, trash, and mounted drives on the desktop. The panel at the top of the screen contains application menus, system tray icons, and workspace switchers.
Terminal Window
The terminal is where you'll do most of your work in Kali Linux. You can open the terminal by clicking its panel icon or pressing Ctrl+Alt+T. The terminal is a powerful tool to run commands, install software, and manage your system.
There are several basic commands that you should learn to navigate the system. Here are a few you can use in terminal:
- ls: Lists all files and directories in the current directory.
- cd: Changes the current directory.
- pwd: Prints the current directory.
- sudo: Executes a command with root privileges.
- apt-get: A package handling utility to install, update, or remove software.
Application Menu
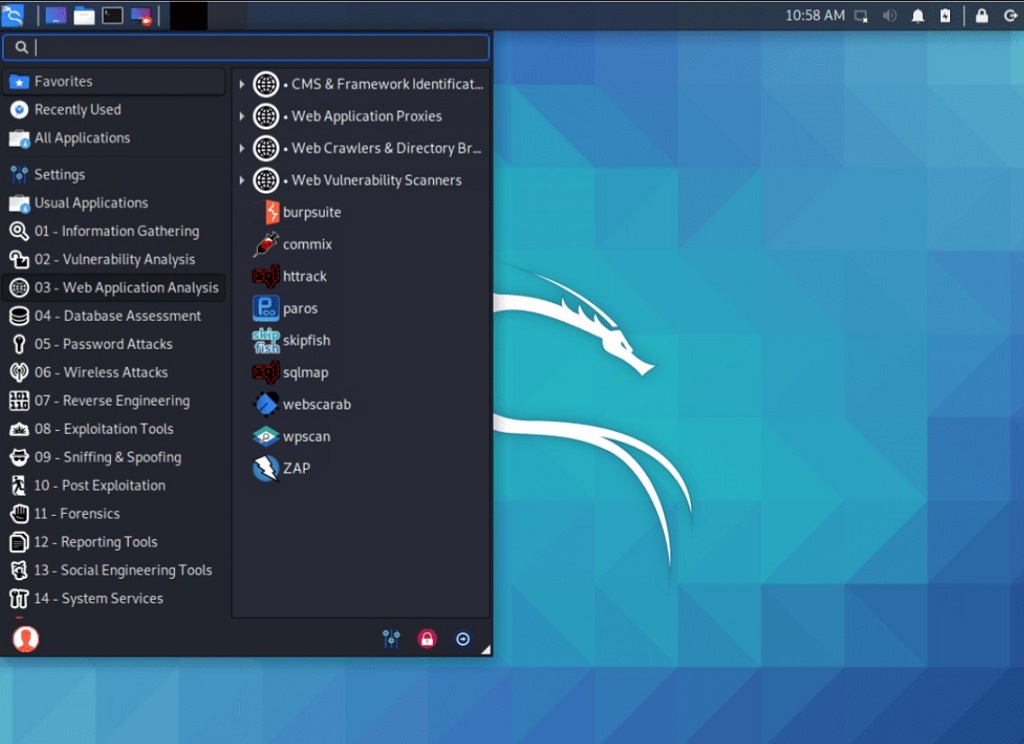
The top application menu contains all the installed applications. They are categorized for easy access. You'll find categories for system settings, accessories, graphics, internet, office, etc.
Environment Customization
You can customize the look and feel of to suit your preferences. Right-click on the desktop and select “Desktop Settings” to change the wallpaper. You can customize the panel, window behavior, and more through the “Settings Manager.”
Remember, the best way to learn is by doing. Feel free to explore and experiment. It's a powerful tool, and you can use it effectively with practice.
Recommended Kali Linux Tools
Kali Linux is known for its wide range of security and penetration testing tools. These tools are what make it a go-to choice for many cybersecurity professionals. Let's look at some of the critical tools and their uses.
Metasploit Framework
Metasploit is one of the most popular tools in Kali Linux. It's a powerful penetration testing tool allows you to find, exploit, and validate vulnerabilities. It provides the ability to write testing scenarios and offers a wide range of plugins that can be used to carry out specific testing techniques.
Wireshark
Wireshark is a network protocol analyzer. It lets you capture and interactively browse the traffic running on a computer network. It's an essential tool for anyone looking to understand network traffic and find potential vulnerabilities or signs of malicious activity.
Nmap
Nmap, or “Network Mapper,” is a free and open-source network discovery and security auditing tool. It can be used to discover hosts and services on a computer network, thus creating a “map” of the network.
Aircrack-ng
Aircrack-ng is a suite of tools for assessing WiFi network security. It focuses on key areas of WiFi security like capturing packets, replay attacks, testing WiFi cards and drivers, and more.
Burp Suite
Burp Suite is a tool for testing web application security. It works as a proxy server between the user's browser and the web application. This allows it to record, analyze, and manipulate all the traffic passing in both directions.
John the Ripper
John the Ripper is a fast password cracker. It's an essential tool for password strength testing and can support many encryption algorithms.
These are just a few of the tools available in Kali Linux. Each tool has its features and uses, so it's worth exploring each. Remember, using these tools responsibly and ethically is of utmost importance. Always ensure you have permission before testing any network or system.
Troubleshooting Common Kali Linux Issues

As a beginner diving into Kali Linux, you might encounter some common issues. Don't worry, we've got you covered! Here are some common problems you may face and their corresponding solutions:
Wireless Network Not Detected
If your wireless network isn't detected in Kali Linux, it could be due to missing or incompatible drivers. Start by checking if Kali Linux supports your wireless card.
Visit the official Kali Linux site or search for compatible drivers online. Installing the appropriate driver should resolve the issue.
Screen Resolution Issues
Sometimes, the screen resolution might not be optimal, resulting in a stretched or distorted display.
To fix this, navigate to the “Display Settings” in the system settings or use the xrandr command in the terminal to adjust the screen resolution to match your display's native resolution.
No Sound Output
If you're not getting any sound output in Kali Linux, the issue might be related to audio drivers. Start by checking the sound settings in the system settings menu and ensure that the correct audio device is selected.
If that doesn't work, you may need to install additional audio drivers specific to your hardware.
Installation Issues
Sometimes, you might encounter difficulties installing software or packages in Kali Linux. The first step is to ensure that your repositories are correctly configured. Use the apt-get update command in the terminal to update the package lists.
If you encounter errors during installation, double-check your internet connection and try installing the software again. If the issue persists, seek help from the Kali Linux community forums or online resources.
Slow Performance
If you're experiencing sluggish performance, it could be due to resource-intensive processes or inadequate system specifications. Close any unnecessary applications or processes running in the background to free up system resources.
Consider allocating more RAM to your Kali Linux virtual machine if you use it in a virtualized environment.
Command Execution Issues
If you're encountering issues executing commands or running scripts, ensure you have the necessary permissions. Use the chmod command to grant executable permissions to scripts. Additionally, ensure you're running commands with appropriate user privileges, such as using sudo for administrative tasks.
Kali Linux User Communities and Forums
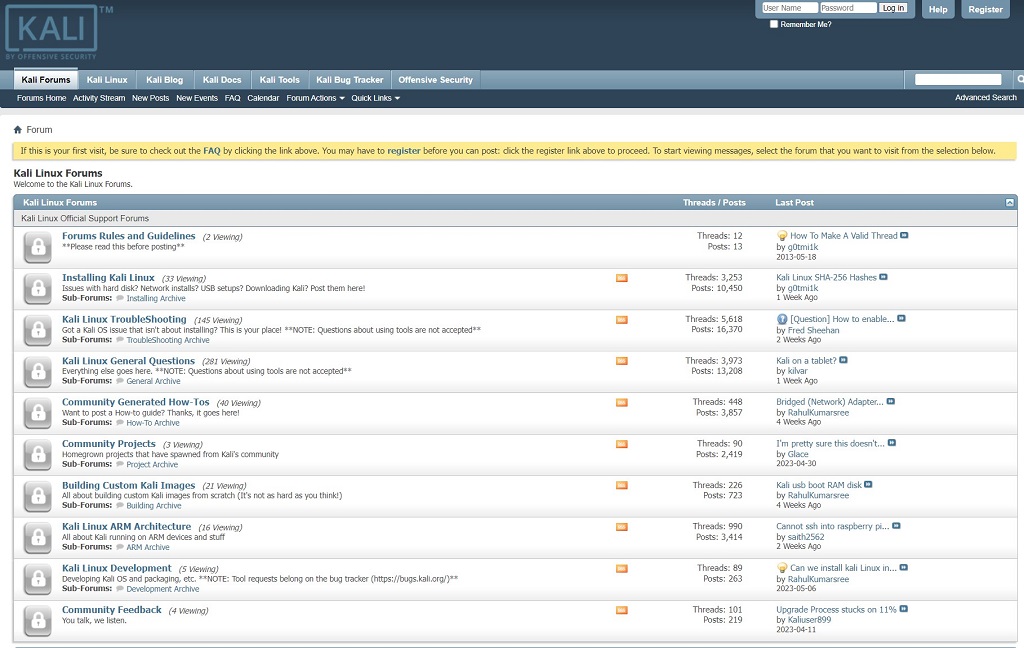
Online communities and forums offer opportunities to connect with fellow users. You can learn from their experiences, and gain valuable insights into using this system for cybersecurity purposes.
Here are several Kali Linux user communities and forums to get you started;
Kali Linux Forums – The official Kali Linux forums provide a platform for users to engage in discussions, ask questions, and share knowledge. It's a great place to find tutorials, guides, and troubleshooting assistance. Visit: https://forums.kali.org/
Kali Linux Subreddit – The Kali Linux subreddit is a community-driven forum on Reddit dedicated to all things related to the OS. Users can ask questions, share tips and tricks, and discuss cybersecurity. Visit: https://www.reddit.com/r/Kalilinux/
Kali Linux Community on GitHub – The Kali Linux community on GitHub is an open-source community where developers and users collaborate on projects related to the OS. You can find tools, scripts, and other resources contributed by the community. Visit: https://github.com/
Offensive Security Community Forums – Offensive Security, the organization behind Kali Linux, hosts community forums where users can discuss various topics related to cybersecurity and penetration testing. It's a valuable resource for learning, sharing ideas, and seeking advice. Visit: https://www.offensive-security.com/community/
Kali Linux Facebook Group – The Kali Linux Facebook group is a community of enthusiasts who share their experiences, ask questions, and support fellow users. It's a platform where you can connect with like-minded individuals and stay updated with the latest news and releases. Visit: https://www.facebook.com/groups/kalilinux/
Twitter Community – Following the official Kali Twitter account (@kalilinux) and engaging with the community on Twitter can provide real-time updates, news, and insights. It's an interactive platform where you can connect with other users, security professionals, and developers in the Linux community. Visit: https://twitter.com/kalilinux
Comparing Kali Linux vs Ubuntu
| Kali Linux | Ubuntu | |
| Purpose | Security and Penetration Testing | General-purpose |
| Target Audience | Cybersecurity professionals | General users |
| Preinstalled Tools | Security tools | Basic applications |
| Security Focus | Extreme security | Broader focus |
| User Interface | For experienced users | User-friendly interface |
| Package Management | Debian system (APT) | Debian system (APT) |
| Release Cycle | Rolling release model | Regular release cycle |
| Support | Community-driven support | Commercial support options |
| Documentation | Extensive | Extensive |
| Customization | Highly customizable | Standard configurations |
| System Requirements | Moderate to high | Moderate |
These distributions are popular Linux-based operating systems but serve different purposes and cater to different user needs.
Kali Linux is designed for security and penetration testing, while Ubuntu is a general-purpose operating system. It's aimed with a narrower focus, specifically on cybersecurity professionals, while Ubuntu caters to a broader audience.
Kali Linux comes with preinstalled security tools, while Ubuntu has a more basic set of applications. Kali Linux has a functional interface, while Ubuntu has a user-friendly interface. Kali Linux follows a rolling release model, while Ubuntu has regular releases.
Both have strong user communities for support. The choice between them depends on your specific needs and technical expertise.
Kali Linux: A Journey Towards Privacy and Protection
In the digital privacy and security world, Kali Linux stands out as a powerful tool for beginners and experts alike. Its extensive security and penetration testing tools empower users to protect their digital assets, identify vulnerabilities, and enhance their understanding of cybersecurity.
Throughout this article, we have explored the fundamentals of this exciting system, its importance in digital security, and how it can be used in practical applications. From network analysis and penetration testing to digital forensics and password testing, Kali Linux offers a wide range of capabilities for securing your digital life.
As you embark on your journey, remember the importance of using it responsibly and ethically. Always obtain proper permissions when conducting security testing, respect the privacy of others, and adhere to applicable laws and regulations.
Stay curious, keep learning, and embrace the power of Kali Linux in your quest for digital privacy and security.