With the rise of cyber threats such as Man-in-the-Middle attacks, protecting your online activities is becoming increasingly necessary. Man-in-the-Middle attacks occur when a hacker intercepts and alters the communication between two parties.
This attack can lead to data theft, financial loss, and other serious consequences. However, using a VPN can help prevent Man-in-the-Middle attacks by encrypting your online traffic and making it difficult for hackers to intercept your data.
This article will explore how a VPN works to prevent Man-in-the-Middle attacks. You'll learn what the advantages and disadvantages of using a VPN are and how to choose the right VPN provider.
What is a Man-in-the-Middle Attack?
According to a report by McAfee, Man-in-the-Middle attacks increased by 27% in the first quarter of 2020 alone. The risk of Man-in-the-Middle attacks will only rise with the rapid increase in remote work, online banking, and online shopping.
Therefore, it is crucial to understand how VPNs can provide an extra layer of security to protect your online activities from these types of attacks.
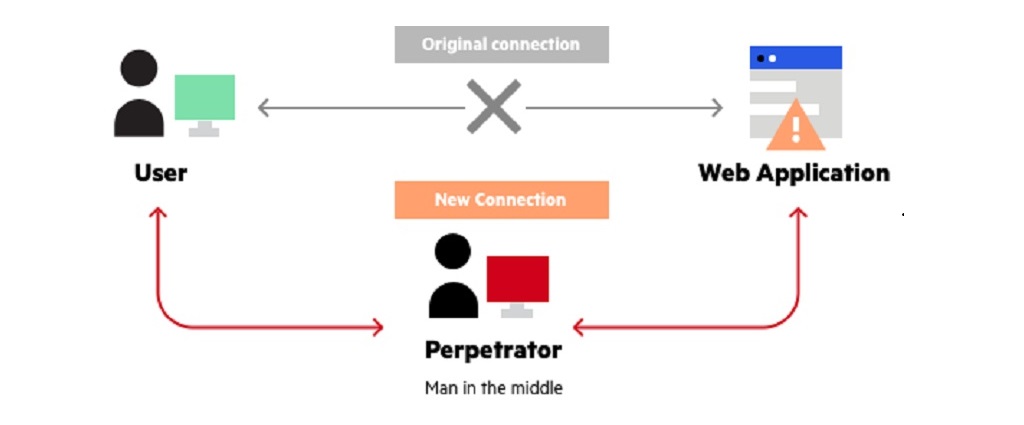
A Man-in-the-Middle (MitM) attack is a type of cyber attack that intercepts data between two parties. This attack can happen during email exchanges, on WiFi networks, or websites. The attacker can secretly relay and possibly alter the communication, allowing them to steal sensitive information or manipulate the conversation.
MiTM attacks are usually stealthy and happen without either party's knowledge. There are several types of Man-in-the-Middle attacks, including:
- IP Spoofing: An attacker impersonates another IP address to gain unauthorized access to a network or intercept communication between two devices.
- DNS Spoofing: The attacker redirects the victim's traffic to a fake website, which looks identical to the original website, and steals sensitive information, such as login credentials.
- HTTPS Spoofing: The attacker intercepts the HTTPS communication and sends a fake HTTPS certificate, tricking the user into believing they are communicating with a legitimate website.
- WiFi Eavesdropping: The attacker intercepts communication over unsecured WiFi networks, such as public WiFi, and steals sensitive information.
- Email Hijacking: The attacker intercepts and alters email communication, enabling them to steal information, modify messages, and impersonate the sender.
MitM attacks can cause significant damage to individuals and businesses, including financial loss, reputational damage, and the exposure of sensitive information. Therefore, it is crucial to take preventative measures, such as using a VPN, to protect against these attacks.
How Virtual Private Networks Prevent MitM Attacks
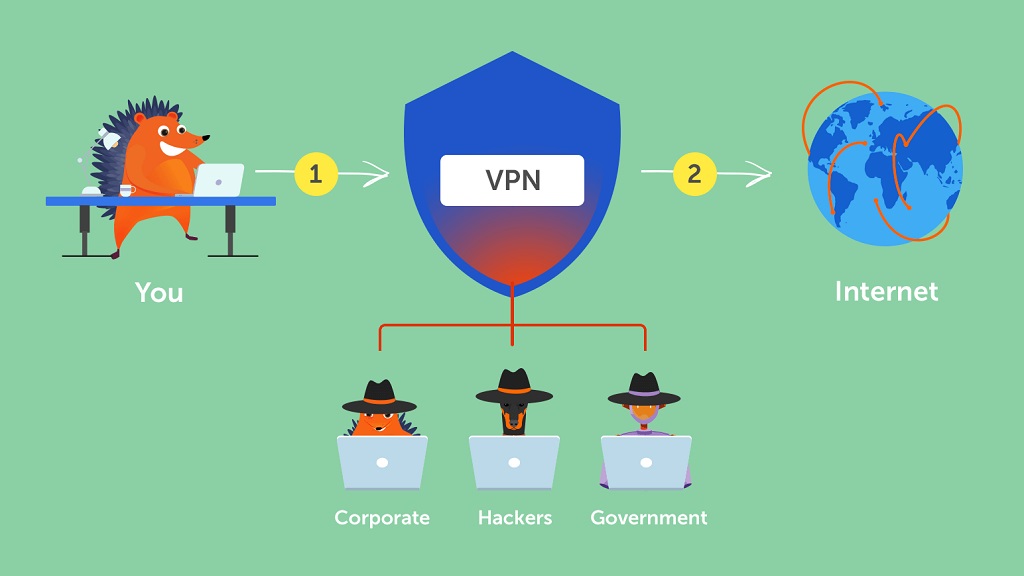
One possible way to increase your resilience against MitM attacks is by using a VPN. Virtual Private Networks encrypt data by creating a secure and private tunnel between your device and the VPN server.
When you connect to a VPN, all of your online traffic is routed through this encrypted tunnel, making it difficult for anyone to intercept or view your data. Although a website Secure Socket Layer (SSL) offers similar protection, not all websites and online applications are guaranteed to be SSL encrypted.
Here's the basic theory of how VPN encryption works with your data;
- Establishing a Secure Connection: When you connect to a VPN server, your device creates a secure connection with the server using an encryption protocol such as SSL, TLS, or IPSec. This connection creates a secure tunnel that prevents anyone from intercepting or viewing your data.
- Encrypting Data: Once the secure connection is established, your online traffic is encrypted before transmitting through the tunnel. Encryption scrambles the data so that it is unreadable to anyone who does not have the encryption key. This makes it extremely difficult for hackers or third parties to intercept and view your data.
- Decrypting Data: When your encrypted data reaches the VPN server, it is decrypted and sent to its intended destination. The VPN server acts as an intermediary between your device and the internet, making it difficult for anyone to trace your online activities back to you.
By encrypting your online traffic, a VPN protects your data from interception, manipulation, and theft by cybercriminals, governments, and other third parties. This provides an extra layer of security that helps to prevent Man-in-the-Middle attacks and other cyber threats.
Role of VPNs in Hiding IP Addresses and Locations
Aside from protecting your data, VPNs also help protect your digital privacy. VPNs play a significant role in hiding IP addresses and locations by providing you with a new IP address associated with the VPN server's location.
When you connect to a VPN, your online traffic moves through the VPN server, and your IP address is replaced with the server's IP address. This process makes it difficult for websites, online services, and other third parties to track your online activities or determine your physical location.
By taking on the IP address of the VPN server, you gain advantages such as location masking, the ability to bypass censorship, and access to geo-blocked websites.
Other Ways to Prevent Man-in-the-Middle Attacks
Although we strongly recommend using a VPN, you can take other steps to help prevent MitM attacks. These include;
Secure Protocols
Secure protocols like HTTPS, TLS, and SSL are essential when sending data over the internet. These protocols encrypt the transmitted data, making it difficult for an attacker to intercept and read it.
In addition to encryption, secure protocols use authentication to ensure that the client and server are who they claim to be. When you visit a website using HTTPS, your web browser verifies the authenticity of the website's SSL/TLS certificate.
This certificate comes from a trusted Certificate Authority (CA) and includes information about the website's domain name, public key, and the CA that issued the certificate. If the browser can't verify the SSL/TLS certificate, it will display an error message and prevent you from accessing the website.
Two-factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring you to enter a second authentication factor besides your password. Even if an attacker manages to intercept the username and password, they still won't be able to log in without the second factor.
The second factor also helps to verify that the user attempting to log in is legitimate. The user must provide something they know (password) and something they have (the second factor), making it more difficult for an attacker to impersonate them.
Secure WiFi Networks
When devices connect to a WiFi network, they exchange information with the access point to establish a secure connection. This information includes a pre-shared key (PSK) or a digital certificate to encrypt and authenticate communication between the device and the access point.
Suppose an attacker attempts to intercept this communication and impersonate the access point. In that case, the device cannot establish a secure connection because the attacker will not have the correct PSK or digital certificate. This prevents the attacker from eavesdropping on or modifying the communication.
In addition to encryption and authentication, a secure WiFi network can also use other security features, such as limiting access to authorized devices and monitoring for suspicious activity, to further prevent MITM attacks.
Be Aware of Phishing Attacks
Phishing attacks are a common way that attackers gain access to sensitive information. Be wary of emails or messages asking you to provide sensitive information or click links. Always verify the sender's email address and check the URL of any links before clicking on them.
Keep Software Up-to-date
Keeping your software up-to-date is an essential part of preventing MITM attacks. Software updates often include security patches that address vulnerabilities that attackers could exploit. Constantly update your operating system, applications, and anti-virus software to ensure protection against the latest security threats.
VPNs Provide Significant Advantages to Digital Security
The importance of online security in the context of MITM attacks cannot be overstated. Failing to protect against these attacks can lead to significant financial losses, damage to reputation, and legal liability. Therefore, it is essential to prioritize online security measures to mitigate the risks of MITM attacks.
Security measures such as using a reliable VPN service, strong passwords, enabling two-factor authentication, and keeping software up-to-date can help prevent MitM attacks. Additionally, secure communication protocols such as HTTPS and VPNs can help encrypt communication and protect against eavesdropping and data manipulation.
