VPNs create a secure and encrypted connection between your device and the internet. This connection is partly thanks to sets of rules and guidelines called protocols. However, choosing the best VPN protocol can be challenging since there are several contenders.
VPN protocols have various features and benefits; selecting the right one can be daunting. That's why it's crucial to understand the nuances of various VPN protocols and consider certain factors before deciding.
What are VPN Protocols?
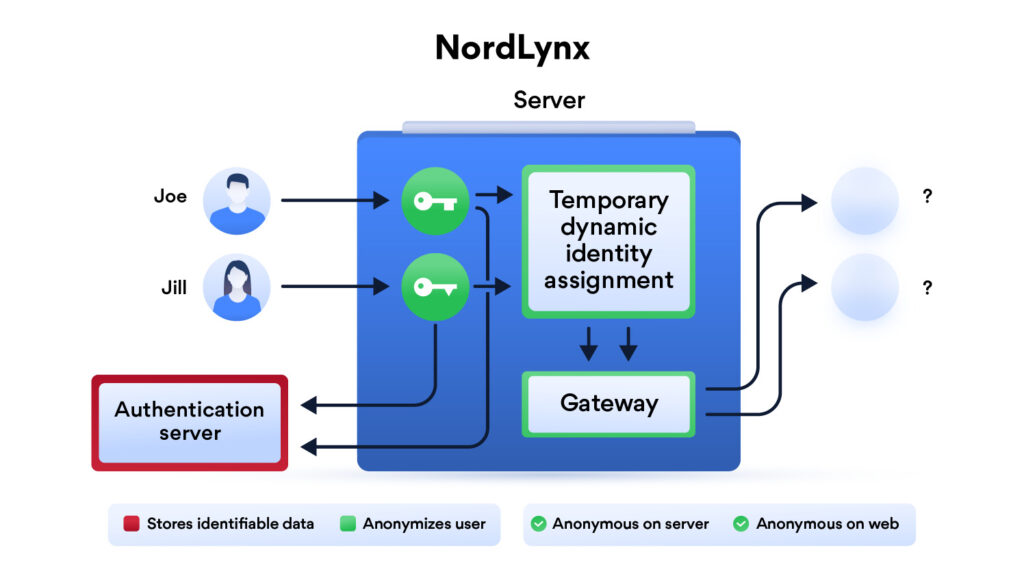
In our exploration of VPN protocols, it's essential to understand what they are and how they function. VPN protocols are rules and procedures that determine how data is transmitted and secured within a VPN connection.
Each protocol utilizes encryption, authentication, and tunneling protocols to establish a secure connection between your device and the VPN server.
How to Choose The Best VPN Protocol
When selecting a VPN protocol, it's essential to consider various factors such as security features, speed and performance, device compatibility, ease of use, and VPN bypass capabilities. Let's compare these protocols based on these criteria:
Security Features
We'll examine the encryption standards, authentication methods, and support for additional security features like Perfect Forward Secrecy (PFS). OpenVPN and IKEv2/IPSec are known for their robust security, while PPTP falls short. Areas of consideration include;
- Encryption Strength
- Authentication Methods
- PFS
Speed and Performance
Factors such as overhead, latency, and bandwidth limitations can affect your browsing experience. OpenVPN and WireGuard typically offer faster speeds due to their optimized code and efficient protocols. Areas of consideration include;
- Overhead and Latency
- Bandwidth Limitations
Device Compatibility
Consider the compatibility of the VPN protocol with your devices and operating systems. PPTP and L2TP/IPSec have broad compatibility, but OpenVPN and WireGuard are supported on multiple platforms, including Windows, macOS, iOS, and Android. Areas of consideration include;
- Device Compatibility and Operating Systems
- Router Support
VPN Bypass Capabilities
If you require VPN bypass capabilities to overcome firewalls or censorship, protocols like SSTP and OpenVPN provide features that can help you navigate such restrictions effectively. Areas of consideration include;
- Ability to Bypass Firewalls and Censorship
- Obfuscation Techniques
- Stealth Mode Features
6 Common VPN Protocols
VPN protocols are essential components of virtual private networks, providing the framework for secure and private communication over the Internet. Here are six common VPN protocols, each with its own set of strengths and weaknesses:
| Protocol | Encryption | Speed | Efficiency | Stability |
| WireGuard | Excellent | Excellent | Excellent | Good |
| OpenVPN | Excellent | Good | Good | Good |
| L2TP | Good | Moderate | Good | Good |
| IKEv2 | Good | Excellent | Good | Excellent |
| PPTP | Poor | Good | Excellent | Moderate |
| SSTP | Good | Moderate | Good | Good |
WireGuard
WireGuard is a modern, open-source VPN protocol designed for simplicity, efficiency, and strong security. It aims to provide a fast and secure tunnel for network communication. WireGuard has gained popularity for its ease of use and high performance.
WireGuard's main strengths lie in its lightweight design, high performance, and ease of use. However, its limited adoption, manual configuration requirements, and lack of certain built-in features may be limiting factors.
Pros
- Lightweight and efficient design
- Strong encryption and secure key exchange
- Simple configuration and easy deployment
- Quick and seamless connection establishment
- Minimal attack surface
- Auditable code
Cons
- Limited adoption
- Limited built-in features
- Lack of support on some older platforms
OpenVPN
OpenVPN is an open-source VPN protocol that provides secure and private communication over the Internet. It uses a custom security protocol based on SSL/TLS for encryption and key exchange.
OpenVPN's main strengths lie in its robust security features, broad platform support, and flexibility in network protocols. However, it may require additional software on specific operating systems and involve a more complex setup than other VPN protocols.
Pros
- Strong security with robust encryption and authentication
- Wide platform support
- Can use different network protocols
- Easy to configure and deploy
- Excellent performance and stability
Cons
- Requires third-party software for setup on some operating systems
- Potential performance degradation over high-latency networks
Internet Key Exchange version 2
IKEv2 is a secure key exchange protocol for establishing and managing VPN connections. It is an enhancement over its predecessor, IKEv1, providing improved security and performance for VPN communication.
IKEv2 combines the features of the Internet Security Association and Key Management Protocol (ISAKMP) and the Oakley protocol. It offers robust security mechanisms, including encryption, integrity checks, and authentication, to establish a secure channel for data transmission.
Pros
- Strong security measures with support for modern cryptographic algorithms
- Efficient and fast reconnections
- Seamless support for mobile devices
- Supports both IPv4 and IPv6 networks
- Support for network mobility and roaming
Cons
- Limited support on older platforms
- Less widely supported compared to other VPN protocols
Layer 2 Tunneling Protocol
L2TP is a networking protocol that operates at the data link layer of the OSI model. It allows the creation of virtual private networks (VPNs) over public networks, such as the Internet, by encapsulating data packets within a secure tunnel.
L2TP combines the best features of two other protocols: Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Forwarding (L2F).
Pros
- Broad compatibility
- Secure and encrypted data transmission
- Multiple authentication methods
- Easily bypasses network address translation (NAT) and firewalls
- Good performance
Cons
- Lacks built-in encryption
- Vulnerable to specific attacks, such as brute force and DoS
Point-to-Point Tunneling Protocol
PPTP is a widely used VPN protocol that operates at the data link layer of the OSI model. It offers a straightforward method for establishing secure connections over the internet.
While PPTP is easy to use and widely supported, its security weaknesses and lack of advanced features make it less suitable for situations requiring strong encryption and secure data transmission.
Pros
- Wide compatibility
- Easy to set up and configure
- Efficient performance for general browsing and light usage
- Native support in many operating systems
Cons
- Security vulnerabilities and weak encryption
- Easily blocked or restricted by some firewalls
Secure Socket Tunneling Protocol
SSTP is a protocol developed by Microsoft and is primarily used on Windows operating systems. It uses SSL/TLS for encryption and is designed to provide secure and private communication between client and server.
The main advantage of SSTP lies in its robust security, native Windows support, and ability to bypass network restrictions. However, its limited platform support, closed-source nature, and potential performance limitations are notable drawbacks.
Pros
- Strong security with SSL/TLS
- Built-in support in Windows
- Firewall-friendly and can bypass network restrictions
- Can use existing SSL certificates for authentication
- Excellent performance and stability
Cons
- Limited platform support outside of Windows
- Lack of transparency and limited scrutiny
Case Studies: VPN Protocol for Different Scenarios
You can choose the VPN protocol that best suits your requirements by considering different scenarios' specific needs and priorities. Tailoring the VPN protocol to your unique situation will ensure a secure and efficient online experience, regardless of your usage scenario.
Best VPN Protocol for Privacy: OpenVPN or WireGuard
Protocols like OpenVPN and WireGuard are excellent choices for individuals who prioritize privacy and anonymity. Their strong encryption, support for Perfect Forward Secrecy, and robust security features ensure your online activities remain private.
OpenVPN's widespread compatibility and extensive community support make it a popular option. WireGuard, with its simplicity and efficiency, offers a promising alternative for privacy-conscious users.
Best VPN Protocol for Gamers and Streamers: OpenVPN, WireGuard, or IKEv2
Gamers and streamers require a VPN protocol that balances security and performance. OpenVPN and WireGuard are suitable options due to their robust security features and relatively low impact on latency.
Meanwhile, games on mobile devices can opt for IKEv2 if their devices or VPN provider doesn't yet support WireGuard.
These protocols offer stable and secure connections, allowing gamers to play online without compromising privacy. WireGuard's lightweight nature makes it a favorable choice for gamers and streamers who prioritize speed and responsiveness.
Best VPN Protocol for Businesses: OpenVPN, SSTP, or IKEv2
In a corporate setting, security, compatibility, and ease of use are paramount. VPN protocols like IKEv2 and SSTP are often preferred due to their robust security features and compatibility with Windows operating systems.
These protocols offer reliable encryption and are supported by various enterprise-grade VPN clients. OpenVPN also finds popularity in business environments, providing high customization and integration options.
Best VPN Protocol for Remote Workers: OpenVPN or IKEv2
Remote workers require VPN protocols that ensure the security and reliability of their connections. OpenVPN and IKEv2/IPSec are commonly used in remote work scenarios due to their strong encryption and support for PFS.
These protocols offer stable connections, allowing remote workers to access corporate resources securely. WireGuard's simplicity and low resource usage make it an attractive option for remote workers seeking efficient connections.
Best Protocol for Travel: OpenVPN, IKEv2, or SSTP
Travelers and tourists often rely on public Wi-Fi networks, which can be vulnerable to cyber threats. VPN protocols like OpenVPN and IKEv2 provide robust security and encryption, safeguarding sensitive data using public networks.
The broad compatibility of these protocols ensures that you can secure your connections across various devices while on the go. Furthermore, protocols with bypass capabilities, such as SSTP and OpenVPN, can benefit travelers. They offer the ability to overcome network restrictions and censorship certain countries impose.
Which VPN Protocol is Right for You?
As we wrap up this article, we hope you feel more confident about choosing the right VPN protocol for your needs. Remember, it's all about finding the perfect balance between security, compatibility, performance, and ease of use.
Ultimately, your VPN protocol choice should align with your specific requirements and provide a secure and seamless browsing experience.
Remember that the VPN landscape is ever-evolving, and new protocols may emerge. Stay informed and periodically reassess your options to ensure you utilize the most up-to-date and effective solution.
The most secure VPN protocol is generally considered to be OpenVPN. Another strong contender is WireGuard. WireGuard is notable for its simplicity and speed. However, WireGuard is also new and less well-tested than OpenVPN.
The fastest VPN protocol is often considered to be WireGuard. WireGuard has a very lean codebase. This contributes to WIreGuard's speed and efficiency. Its modern cryptographic algorithms also enhance its performance.
L2TP uses IPSec as its data encryption mechanism. This is because L2TP does not provide encryption. It relies on the IPSec protocol for encryption and secure data transmission. The protocol is widely supported across various platforms.
Developed in the mid-1990s, PPTP was one of the first protocols to enable VPN connections. However, its age is a significant factor in its security vulnerabilities. It uses the MS-CHAP v2 authentication protocol, known for its vulnerabilities.
For Windows VPN clients, OpenVPN is often recommended as the preferred protocol. Notably, it's robust, well-tested, and relatively fast. However, WireGuard is quickly gaining popularity due to its superior speed and efficiency in comparison.
