Social engineering is one of the most critical vectors in cyber security. It targets the most vulnerable and unpredictable element of any security system: humans. No matter how robust a system's defenses are, the people using it are often the weakest link.
While not a new concept, social engineering has gained significant traction due to the increasing sophistication and frequency of cyber attacks. Understanding social engineering is not just a matter of technical knowledge; it's about understanding human behavior and how it is manipulated.
Social Engineering: What is It?
In the context of cyber security, social engineering is a method of manipulating individuals into divulging confidential or personal information that may be used for fraud. It's not about cracking codes or exploiting software. Instead, social engineering tries to exploit humans.
The social engineer, much like a con artist, manipulates people into breaking standard security procedures, often without the person even realizing they've been tricked. The goal is usually to gain unauthorized access to systems or data, but the methods used are psychological, not technical.
How Social Engineering Exploits Human Psychology
The success of social engineering hinges on the ability to exploit common aspects of human nature. Social engineers prey on various human traits, such as trust, fear, curiosity, ignorance, or the natural desire to be helpful.
For instance, a social engineer might impersonate a trusted figure to exploit an individual's trust or create a sense of urgency to provoke immediate action without proper scrutiny. By understanding these psychological triggers, social engineers can craft convincing scams.
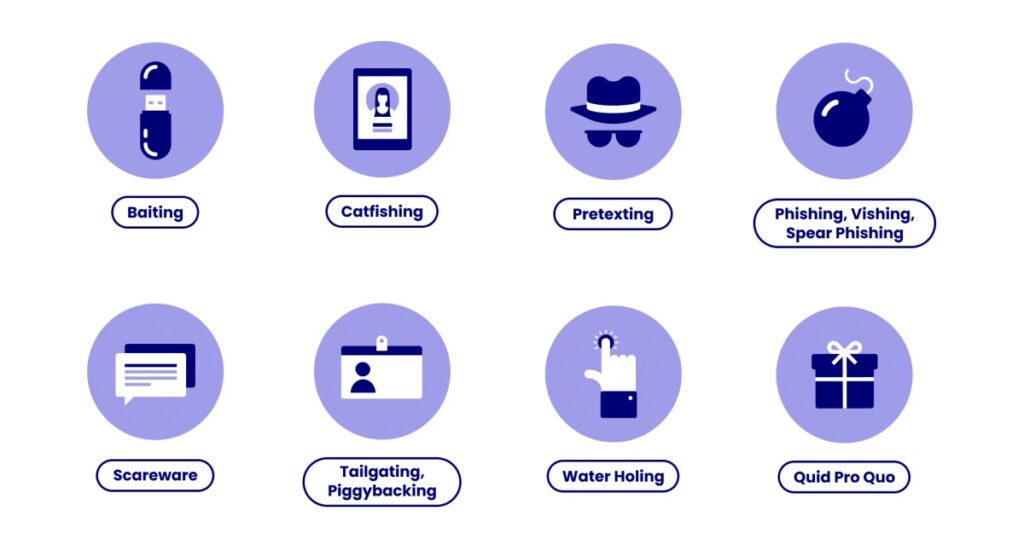
Types of Social Engineering Attacks
According to Verizon's 2020 Data Breach Investigations Report, social engineering attacks accounted for 22% of all data breaches. Phishing, a type of social engineering, was present in 96% of incidents where data was stolen.
Social engineering attacks come in various forms, uniquely crafted to exploit human psychology and manipulate individuals into revealing sensitive information. Here's a more in-depth look at some of the most common types:
Phishing
Phishing is arguably the most prevalent type of social engineering attack. It typically involves sending fraudulent emails that appear to come from a legitimate source, such as a bank, a trusted company, or a familiar individual.
The goal is to trick recipients into revealing personal information, such as passwords, credit card numbers, or social security numbers. Phishing emails often create a sense of urgency, prompting the recipient to act immediately.
For instance, an email might warn of a security breach and ask recipients to change their passwords immediately, leading them to a fake website to capture their credentials.
Spear Phishing
This is a more targeted form of phishing where the attacker has taken the time to research their victim and personalize their attack. This could involve using the victim's name, position, or other personal information to make the attack more convincing.
Spear phishing attacks are often harder to detect because of their personalized nature.
Pretexting
In pretexting attacks, the attacker creates a fabricated scenario or pretext to steal the victim's personal information. They might impersonate a co-worker, a police officer, a bank official, or anyone else who could have a supposed legitimate need for the victim's information.
For example, an attacker might call a victim pretending to be a tax official needing to confirm some details. The attacker builds a believable story to obtain the information they want.
Baiting
Baiting involves offering something enticing to the victim to gain access to their login credentials or personal information. This could be a free download, a lottery win, or any other too-good-to-be-true offer.
For instance, an attacker might leave a USB drive labeled “Confidential” in a place where it's sure to be found. Curiosity might lead the finder to insert the drive into a computer, unwittingly installing malware that gives the attacker access to the system.
Quid Pro Quo
In this attack, the social engineer offers a service or benefit in exchange for information or access.
For example, they might offer tech support in exchange for the victim's login credentials. The attacker might call random numbers within a company claiming to be calling back from technical support.
Eventually, they might find someone with a genuine problem, grateful that help has arrived.
Tailgating or Piggybacking
This is a physical form of social engineering where an unauthorized person follows an authorized person into a restricted area.
For example, the attacker might walk behind a person entering a secure building or server room. While it's not as common as the other types, it's a stark reminder that social engineering can take many forms, not all digital.
Real-life Examples of Social Engineering Attacks
I remember a time when I received a call from someone claiming to be from my internet service provider. They said they were offering a free upgrade to my internet package. I had to provide them with my username and password to confirm my account.
It may sound funny, but most won't laugh when something like this happens to them. Worse, social engineering attempts like this have succeeded multiple times. Not just against individuals but massive organizations, including those with significant security blocks in place.
The incidents below showcase examples of successful social engineering attacks. But remember, this is just the tip of the iceberg.
Case Study 1: 2016 Phishing Attack on John Podesta
One of the most notorious phishing attacks in recent history was the 2016 attack on John Podesta, the chairman of Hillary Clinton's presidential campaign. The attackers sent Podesta an email that appeared to come from Google.
The email warned him of a potential security breach and urged him to change his password immediately. The email contained a link to a fake Google login page, where Podesta unwittingly entered his existing password, giving the attackers access to his email account.
The incident underscores the effectiveness of phishing attacks and the importance of scrutinizing unexpected emails, even those that seem to come from trusted sources.
Case Study 2: Hackers Accessing IRS Database in 2015
In 2015, a group of hackers used pretexting to access the personal tax information of 114,000 individuals from the US Internal Revenue Service (IRS).
The attackers posed as taxpayers, using previously stolen identity information to authenticate themselves on the IRS's “Get Transcript” service. This incident highlights the dangers of pretexting and the importance of using multiple layers of authentication to protect sensitive information.
Case Study 3: US DOD Baiting Attack
In a famous baiting case, the US Department of Defense was targeted in 2008 when flash drives were left in parking lots. Curious employees picked up the drives and plugged them into their computers, unintentionally installing a malicious code that spread throughout the network.
This case demonstrates how curiosity can be exploited in a baiting attack and emphasizes the importance of cautiously handling unfamiliar devices.
How to Protect Yourself from Social Engineering Attacks
The first line of defense against social engineering is education and awareness. Individuals and organizations must understand what social engineering is, how it works, and the various forms it can take.
Regular training sessions can help employees recognize the signs of a social engineering attack and understand the proper response. These sessions should include real-world examples and scenarios to make the training as practical and relevant as possible.
Other ways you can defend against social engineering attacks include following best practices for cyber hygiene, such as;
Use Strong, Unique Passwords: Using a unique password for each account can prevent an attacker from gaining access to all your accounts if one is compromised. Consider using a password manager to keep track of your passwords.
Enable Two-Factor Authentication: Two-factor authentication adds an extra layer of security by requiring a second form of identification in addition to your password.
Be Wary of Unsolicited Communications: Be cautious of unsolicited phone calls, emails, or messages asking for personal or financial information. Always verify the source before providing any information.
Keep Your Software Updated: Regularly update your software, including your operating system, browser, and antivirus program. These updates often include security patches for known vulnerabilities that attackers could exploit.
Use a VPN: Using a VPN as part of a broader security strategy can add protection to your online activities. While it won't directly protect you against social engineering attacks, it helps makes it much harder for third parties to track your online activities or steal your information.
Wrapping Up: The Human Element in Cyber Security
Given the increasing number of cyber threats, understanding social engineering is more critical than ever. As we've seen, these attacks exploit human psychology to trick individuals into giving up sensitive information, bypassing even the most robust technical defenses.
By recognizing the signs of social engineering and following best practices for cyber hygiene, we can significantly reduce the risk of falling victim to these attacks.
While technology is crucial in protecting our data, the human element remains the most vulnerable aspect of any security system. Therefore, continuous education and vigilance are our best defenses against the ever-evolving threat of social engineering.