As cyber threats evolve, the most pressing question has been whether traditional passwords are enough to protect us. Enter the concept of Passkeys—a term that's been around for some time but is only now beginning to see more significant implementation.
But what exactly is a Passkey, and could it be the harbinger of a future where passwords become obsolete? Rather than seeing it as a password replacement, passkeys are an evolutionary step in personal digital security.
What is a Passkey?
A passkey is a temporary code or digital key to authenticate a user or device. Compared to traditional passwords, passkeys are often dynamic and short-lived. The primary strength of passkeys is that they incorporate various layers of authentication.
This concept makes passkeys dynamic and multifaceted. They can be a combination of something you know, something you have, and something you are—thus offering a more well-rounded approach to security.
Common Passkey Features
A passkey, while serving a similar purpose as a password, has distinct features that set it apart. Understanding these features can help users decide when and how to use passkeys for their security needs. Passkeys are often;
- Generated dynamically
- Shorter in length than passwords
- Time-sensitive / single use
- Can work combined with other authentication methods
- Easy to use
Types of Passkeys
Passkeys come in various forms, each with its unique features and advantages. Here are some of the most common types:
One-Time Passkeys
These are dynamically generated codes valid for a limited period or a single transaction. They are often sent to the user via SMS or an authenticator app and must be entered with the regular password.
Examples of One-Time passkeys include;
- SMS Verification Code: When logging into a banking app, a one-time code is sent to the registered mobile number. The code expires after a few minutes.
- Email Verification Code: Some services send a temporary code to your email that you must enter within a specific time frame to authenticate yourself.
- Transaction Authentication Number (TAN): In online banking, a unique code is generated for each transaction and sent to the user for approval.
Biometric Passkeys

Biometric authentication uses unique physical characteristics like fingerprints, facial recognition, or iris scans as a form of Passkey. Since these traits are unique to each individual, they offer high security.
Examples of Biometric passkeys include;
- Fingerprint Scanner: In smartphones and laptops, the device scans your fingerprint to grant access.
- Facial Recognition: iPhones and other devices use facial recognition technology as a secure way to unlock the device.
- Iris Scan: Some high-security systems and even smartphones use iris scans for authentication.
Hardware-Based Passkeys
Passkeys based on hardware involve a physical device, such as a smart card or a USB security key, to authenticate the user. The device serves as a second layer of security, often in conjunction with a traditional password or PIN.
Examples of hardware-based passkeys include;
- YubiKey: A physical USB device that you insert into your computer as a form of two-factor authentication.
- Smart Card: Used often in corporate settings, a smart card is inserted into a reader as an additional layer of security.
- NFC Tags: Near Field Communication (NFC) tags can be used as a secure method to unlock doors or even authenticate payment transactions when tapped against a compatible reader.
How Passkeys Work
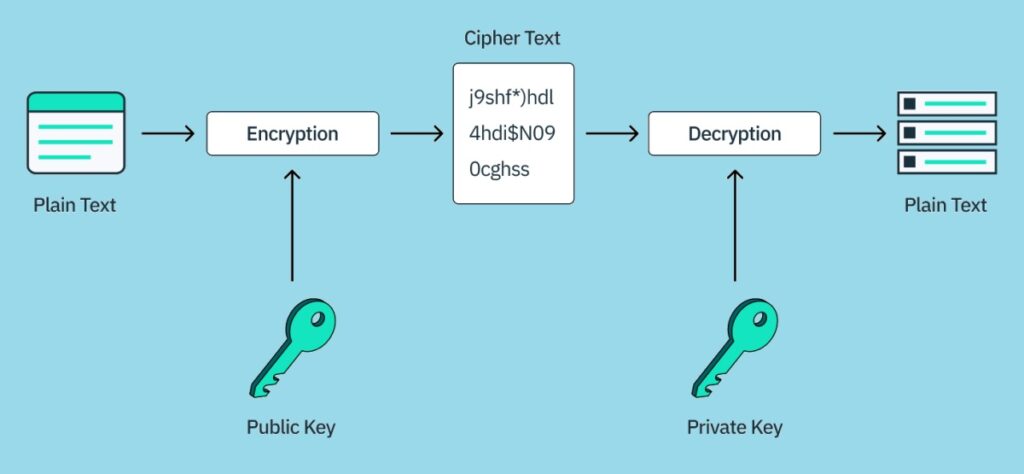
The underlying technology of Passkeys varies depending on the type, but the core principle remains the same: multi-layered authentication. Here's a simplified breakdown of how Passkeys work:
- Initial Authentication: The user enters a traditional password or PIN, something they know.
- Secondary Verification: An additional layer of authentication kicks in. This could be a one-time code sent to the user's phone or a prompt for biometric verification.
- Final Confirmation: Once both layers are authenticated, the user gains access to the account or system.
Passkeys vs. Password: What's The Difference?
| Passwords | Passkeys | |
| Authentication | Single-Factor | Multi-Factor |
| Complexity | Static | Dynamic |
| User Involvement | Requires Memorization | Less Cognitive Effort |
| Security | Susceptible to Phishing, Brute-Force | Layered Security |
| Recovery | Secondary Email | Multi-Step Verification |
| Current Use | Common | Emerging |
While a passkey and password serve the same ultimate purpose—to authenticate users and grant access to systems—they do so in markedly different ways. Understanding the differences is essential to deciding if you want to migrate to a passwordless future with passkeys.
Many significant differences exist, which we'll simplify as follows;
How They Handle Authentication
Traditional passwords rely on a single-factor authentication model based on something you know. This could be a string of characters, numbers, or both. The onus is on you to remember this information accurately.
Passkeys, on the other hand, often employ multi-factor authentication, incorporating something you know (like a PIN or password), something you have (like a mobile device or hardware key), and sometimes even something you are (like a fingerprint or facial scan).
How Safe They Are
Passwords are generally static, meaning they remain the same until the user decides to change them. This static nature makes them vulnerable to various cyberattacks, such as brute-force attacks and phishing.
Passkeys are often dynamic, especially in the case of one-time codes. They change periodically or are valid for a limited time, making them more resistant to attacks. Passkeys also offer layered security. Even if one layer is compromised, the additional layers provide a safety net
Your Involvement in The Process
Passwords require you to remember and manage them. This often triggers password fatigue, especially when users have multiple accounts across different platforms. Even I gave up and ended up using a secure password manager.
Passkeys, particularly biometric or hardware-based, require less cognitive effort from the user. Biometric data doesn't need to be remembered, and hardware keys can be easily carried around.
State of The Internet: Usage of Passkeys vs. Passwords
Passwords have been the default standard for digital authentication for decades. Every online platform, from social media to online banking, employs passwords to secure user accounts.
According to various studies, billions of password-protected accounts are worldwide, underscoring their ubiquity.
While Passkeys are still in the nascent stages of adoption, their usage is growing, especially in sectors requiring high-security levels. According to recent surveys, adopting multi-factor authentication, which often involves Passkeys, has seen a significant uptick in the past few years.
Are Passkeys a Bulletproof Security Solution?
While Passkeys offer a promising alternative to traditional passwords, they have challenges and limitations. As with any emerging technology, there are hurdles and questions to answer.
Some challenges that currently face passkey advocates include;
Infrastructure Overhaul
Adopting Passkeys often requires a complete overhaul of existing authentication infrastructure. This can be time-consuming and costly, especially for large organizations with legacy systems.
Compatibility Issues
Not all systems and devices can handle multi-factor authentication or biometric data, leading to compatibility issues that can hinder widespread adoption.
Learning Curve
For many users, especially those who are less tech-savvy, understanding the nuances of Passkeys and how to use them effectively can present a steep learning curve.
Privacy Concerns
In an age where data is the new oil, the security of user data is a paramount consideration in almost all industries. That's especially true where cybersecurity is related. Passkeys currently face several privacy challenges, such as data storage and tracking.
Best Practices When Using Passkeys
Passkeys, with their temporary and dynamic nature, offer a unique layer of security in the digital realm. However, to maximize their effectiveness and ensure optimal protection, users should adhere to certain best practices:
Ensure Secure Delivery Channels
- Always ensure that the medium through which you receive the passkey is secure. For instance, if you receive passkeys via SMS, ensure your phone's messaging app is malware-free.
- Consider using encrypted communication apps or platforms that offer end-to-end encryption for receiving passkeys.
Use Passkeys Promptly
- Passkeys are often time-sensitive. Use them promptly after receipt to reduce the risk of them being intercepted or becoming invalid.
- Avoid saving passkeys in easily accessible places, such as sticky notes or unencrypted digital notes.
Beware of Phishing Attempts
- Cybercriminals often pose as legitimate entities to extract sensitive information, including passkeys. Always verify the source before providing your passkey.
- Be cautious of unsolicited messages or emails prompting you to enter a passkey, especially if you did not initiate an action that requires one.
Combine Passkeys With Other Security Measures
- While passkeys offer an added layer of security, they are most effective when used alongside other authentication methods, such as passwords or biometric verification.
- Consider enabling two-factor or multi-factor authentication on platforms that support it.
Regularly Update Security Protocols
- Ensure the software or platform generating and sending passkeys is regularly updated to incorporate the latest security patches and features.
- Stay informed about security threats and trends to adapt and enhance your passkey-related practices.
Final Thoughts: Should You Replace Your Password With a Passkey?
Given the current landscape, Passkeys and passwords will likely coexist as complementary systems. While Passkeys offer enhanced security, not all platforms and users are ready to switch.
The problem is that many of you face different pressure levels to convert your passwords to passkeys. For example, Google, Apple, and some password managers strongly urge users to switch to passkeys.
Rather than face whether you should switch, ask yourself if you're ready for a world where you must use a combination of passkeys and passwords. After all, the former is still in its infancy, and only a few sites and applications support them.